Updating Palo Alto HA Firewalls
In this article, we’ll update an Active/Passive pair of Palo Alto Firewalls, without running Panorama.
In this article, we’re updating from 8.0 to 8.1.
Selecting a Version
When choosing a version, refer to the End-of-Life Summary guide. This shows the end of life date for each major version.
Keep in mind that the latest version is not always going to be supported the longest. For example, version 8.1 will be supported until 2022, while 9.0 is supported until 2021.
Unless there’s a particular feature you need, try to stick with the Long Term Support version.
Upgrade Path
Feature releases cannot be skipped. For example, to get from 8.0 to 9.0, first upgrade to 8.1, then upgrade to 9.1.
It is Palo Alto’s recommendation to update to the base release in the next feature release version, and then perform a separate upgrade to your target version.
In our example, we’re upgrading from 8.0.1 to 8.1, so we would first upgrade to 8.1.0, and then upgrade to 8.1.10 (the latest 8.1.x release at the time of writing).
Remember to read the release notes for the version you want to update to.
Minimize Downtime
When using HA, one node can be upgraded at a time, which minimizes downtime.
Plan to start on the passive node, and when it’s upgraded, perform a failover. Then upgrade the other node.
For active/active, it doesn’t matter which node is upgraded first, but it is recommended to start with the secondary.
NOTE: Even with the lower risk of downtime, a few packets can be dropped during failover, so schedule the update during a maintenance window.
Update Process
Download Updates
Log onto each firewall (Active and Passive), and check that the versions you need are downloaded.
If they’re not, download them now.
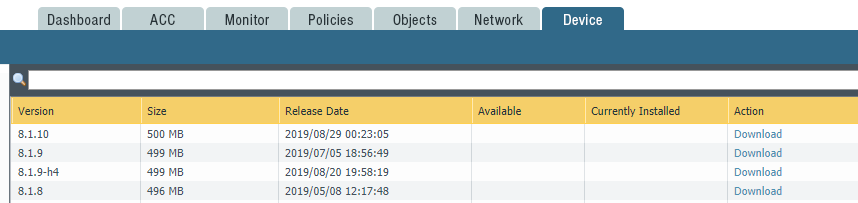
Also check if the Applications and Threats updates have been installed. These should be up to date before running the PAN-OS update.
To check, navigate to Device > Dynamic Updates, and check the release date of the installed version.
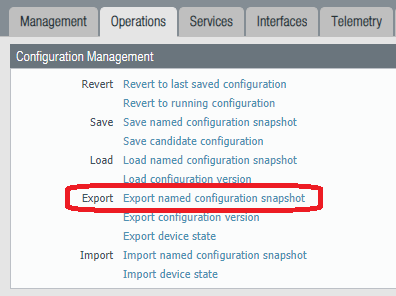
Create a Backup
Browse to Device > Setup, and then to the Operations tab.
Click Export named configuration snapshot.
Disable Preemption
Normally, preemption is on. This enables the passive firewall to automatically take over if the active firewall fails.
For the duration of the update, disable preemption.
Device > High Availability > General > Election Settings
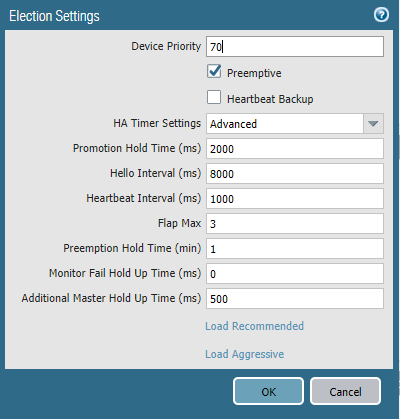
When this is done, commit the config, and confirm the config is replicated to the passive unit.
Installing the Update
Log on to the passive unit, and install the update.
Device > Software.
Select to base of the new feature release (for example, 8.1.0) and click Install.
Once the install is completed, restart the firewall. After the reboot is complete, log on to the firewall, and confirm the device is healthy and running the correct version.
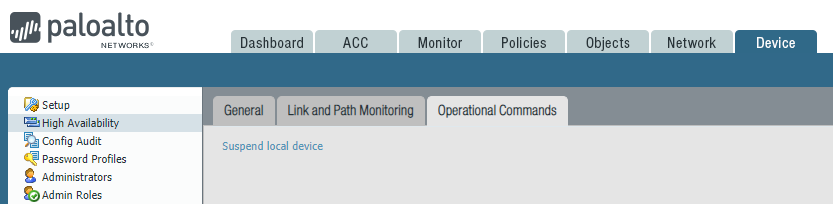
Now, log on to the active unit, and ‘suspend’ the active peer to cause a failover. This is done so the updated device will accept and pass traffic while the other unit is being updated.
Device > High Availability > Operational Commands. Click Suspend local device.
Now, install the update on the second unit, and reboot.
Once this is back up and you’ve confirmed the health, you can now upgrade to the next version.
Restore HA State
On the firewall that was just updated, log on to the CLI and run:
request high-availability state functional
This re-enables high availability.
Finally, enable HA preemption once again.
References
Palo Alto – Upgrade an HA Firewall Pair to PAN-OS 8.1
Palo Alto – Determine the Upgrade Path to PAN-OS 8.1
Palo Alto – Determine the Upgrade Path to PAN-OS 9.0
Palo Alto – End of Life Summary
Palo Alto – How to Recover HA Pair Member From the Suspended State