Hierarchical Network Model
Last Updated: [last-modified] (UTC)
The campus network needs a good structure. Devices roam the network. Users hold phone called and video conferences in real time. And, there’s usually a guest WiFi to secure. These are a few aspects that benefit from using a hierarchical network model.
This model is not new though. It has been in use for years, and has proven itself. This model provides us with a reference topology that separates the network into layers. Each layer has its own goals and functions. This assists in making the network scalable, stable, and deterministic. Following this model allows the designer to keep the network as simple as possible. This avoids a spiders-web of equipment, linked together in an adhoc style.
Deterministic vs Non-Deterministic
If a network is designed to be deterministic, any change to the network has well-known and predictable outcomes.
A non-deterministic network leaves a doubt in the network admins mind as to the result of a change.
If someone asks ‘what will happen if Switch-A were to fail?’, and your response is ‘It depends on…’, then your network is non-deterministic
Network Layers
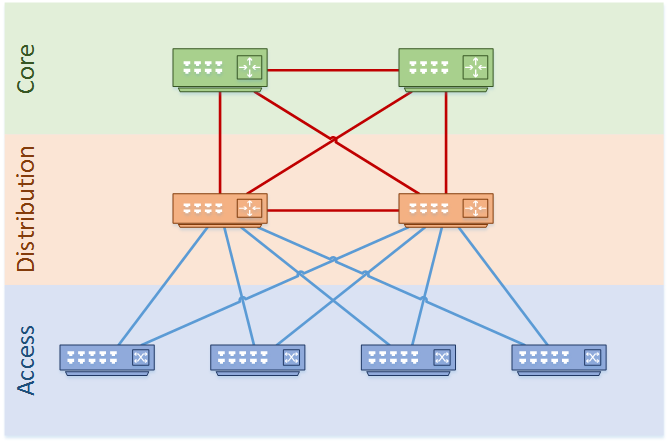
As shown below, the hierarchical network model uses three layers. These are the Core, Distribution, and Access layers.
Often, these layers, map to the physical layout of the network. As you will see later, this is not always the case, so try to think of them as logical layers.
The requirements and functions of each layer is different. To address this, the design approach to each layer needs to be different too.
Access
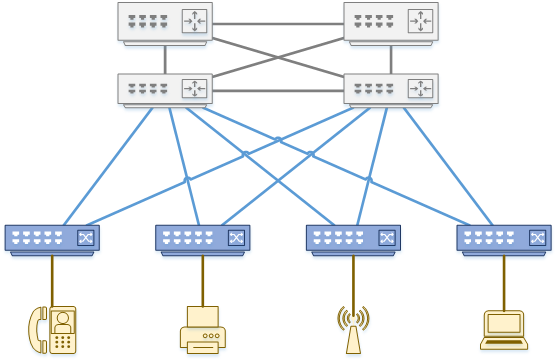
The access layer is dedicated to meeting the needs of end-device connectivity
The access layer is the edge of the network where host devices connect. This includes workstations, and printers. Devices that extend the network, such as Phones, and Access Points, also attach here.
This is the layer where the admin spends most of their time. It is a very feature rich layer, as it needs to support so many different endpoints. As it’s the network edge, it’s the first line of defense for security, and is a logical QoS trust boundary.
This layer typically includes services such as:
- Discovery and configuration – CDP and LLDP
- Security and network identity – 802.1x, port security, DHCP snooping, DAI, Dource Guard, Idendity Based Network Services, and Web-auth
- Application recognition – QoS marking, policing, queueing, NBAR
- Network control – Routing protocols, spanning-tree, DTP, LACP, UDLD, FlexLink
- Physical infrastructure – PoE
The Access layer connects northbound to the distribution layer. The connections may be layer-2 trunk ports, or layer-3 routed ports. Deciding between layer-2 and layer-3 is an important design choice. This is covered in another article.
Devices connect to the access switches at layer-2.
Distribution
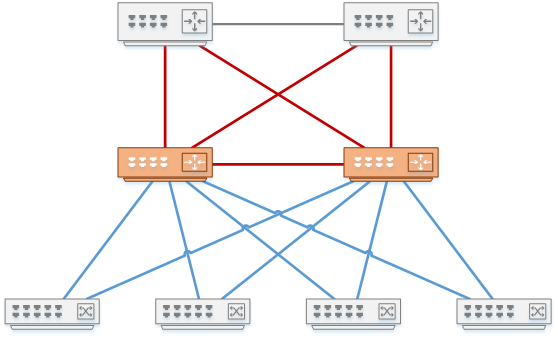
The distribution layer creates a distribution block, and aggregates traffic to the rest of the network
The distribution layer is a multi-purpose layer. In particular, it needs to aggregate access layer traffic, and forward it to the rest of the network. There are likely many access layer switches in the network. Each of these switches has uplinks to the distribution layer switches. Many end devices across access layer switches are aggregated at the distribution layer.
Using distribution switches to aggregate traffic logically creates ‘distribution blocks’. Consider a campus with four buildings. Each building has two distribution switches, and eight access layer switches. Each of these buildings is a distribution block. Traffic can route between distribution blocks through the core layer.
Distribution blocks are useful to avoid ‘fate sharing’. Imagine a case where there is a switching loop in one distribution block. This type of error is isolated to this one block, the rest of the network does not share the same ‘fate’.
The distribution layer provides a demarcation point between the block and the rest of the network. This makes it a good place to apply network policies. It is also a nice security boundary between the access layer and the rest of the network.
The features in the distribution layer depend on the design of the core layer and the access layer. For example, if EIGRP runs in the core, then the distribution layer should also run EIGRP. If the access layer needs 10G ethernet, then the distribution layer also needs 10G.
The distribution layer always connects to the core through routed ports. This means that the distribution layer switches must use dynamic routing. The distribution layer is an aggregation point for the devices in the access layer. This is also true for dynamic routing. The distribution layer summarizes the access layer addresses toward the core.
The distribution switches use either layer-2 or layer-3 to connect to the access layer. This depends on the access layer design, which is covered in more depth in another article.
Core
The core layer is dedicated to providing non-stop connectivity across the campus network
The core layer is the backbone of the campus network. It interconnects all the distribution blocks. The core layer has a single purpose, and does not need many features. There are no security policies, no QoS, and no endpoints attached.
The key design principles of the core layer is that it must be fast, it must be always available, and it must be reliable. It is critical that there is no single point of failure. If there is a failure, recovery must be as fast as possible.
The core layer does not usually have a lot of configuration. It is also not upgraded unless necessary. It needs to be lean and mean. Often the core uses large chassis based switches, such as the Catalyst 6500 or the 4500-X. An alternative to chassis switches is stack-wise switches.
The core runs pure layer-3 links (routed ports), and highly tuned routing protocols.
Topologies
 The hierarchical model is, as the name suggests, is just a model. In practice, the physical deployment may not match the model exactly.
The hierarchical model is, as the name suggests, is just a model. In practice, the physical deployment may not match the model exactly.
One way to design the network is to use three physical tiers, which maps directly to the model. But, that may not suit everybody. Another way to deploy is the Collapsed Core model.
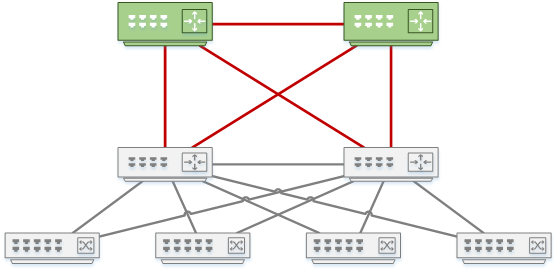
Two-Tier Design: The Collapsed Core
The core layer in the hierarchical model is a logical concept. But ask this question: ‘Does my network need a physical core layer?’ Providing a separate physical core costs more, which not all businesses can justify. Some networks are small enough that they don’t need a physically dedicated core.
Remember how the core provides a backbone for connecting the distribution blocks? Well, it is possible for distribution switches to take on this responsibility themselves.
In the topology below, the campus network has only two distribution blocks. Unless growth is expected, it doesn’t make sense to add in a separate core layer here. When the distribution switches are fully meshed, they provide the core functions themselves.
That’s why this topology is called Collapsed Core. The core and the distribution layers both run on the same physical switches.
The core layer principles still apply in this design. The mesh between the blocks still needs to be highly reliable. It needs to provide fast transport. And it must be very quick to converge.
This design is suitable for a network with no more than 2 or 3 distribution blocks.
When considering this model in your design, think about:
- Scalability – How far can my design grow?
- Planned Expansion – Will the network need to grow in the forseeable future?
- Management – Is this too complex to manage, or simpler than the alternative?
Three-Tier Design
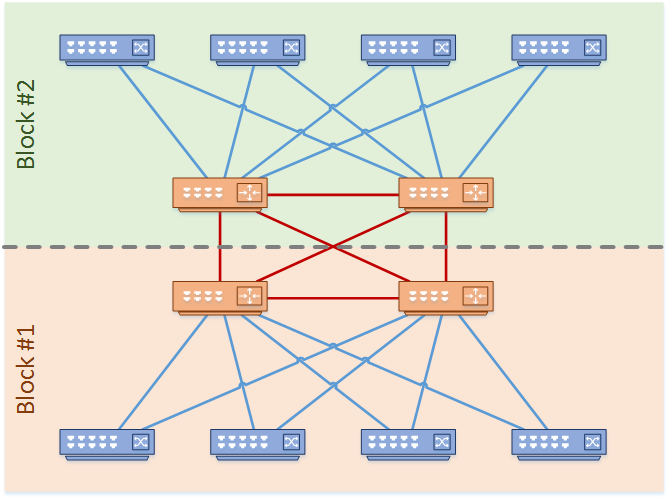
Larger networks will run into problems if they try to use the collapsed core model. Remember the full mesh rule? See what happens when there are four distribution blocks in the network.
The full mesh between the distribution switches is getting too complicated. Not only is it a cabling nightmare, but it is difficult to manage and troubleshoot. Imagine how much worse this gets when adding more distribution blocks.
Now have a look at the same network with a pair of core switches added.
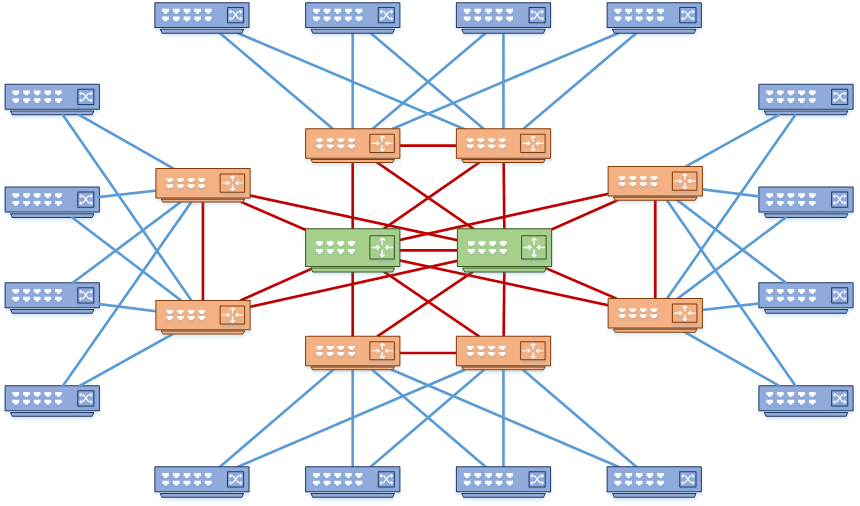
See how the core layer simplifies the topology? Each pair of distribution switches are fully meshed to the core, which is far simpler.
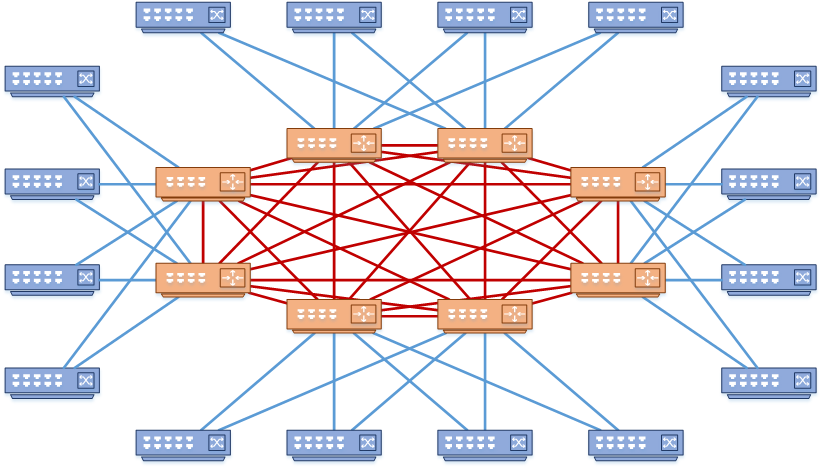
More Than Three Tiers?
 So, what would happen if you have an extremely large network? The core layer would grow, and the full mesh to the distribution switches would become a problem. This might happen if you need to connect several large campus sites. How do you design around that?
So, what would happen if you have an extremely large network? The core layer would grow, and the full mesh to the distribution switches would become a problem. This might happen if you need to connect several large campus sites. How do you design around that?
If needed, the core layer can be broken out into two physical tiers. This makes the core layer more scalable. In design terms, the core layer principles will still apply to both of these tiers.
To see the different design options for hierarchical design, see the article, ‘Hierarchy Design Part 1’
[maxbutton id=”4″ text=”Hierarchy Design” url=”https://networkdirection.net/Hierarchy+Design+Part+1″]
References
Cisco – Enterprise Campus 3.0 Architecture: Overview and Framework
Marwan Al-shawi and Andre Laurent – Designing for Cisco Network Service Architectures (ARCH) Foundation Learning Guide: CCDP ARCH 300-320 (ISBN 158714462X)