ICMP For IPv4
Last Updated: [last-modified] (UTC)
The Basics of ICMP
ICMP (Internet Control Message Protocol) was released way back in September 1981 as part of RFC 792. It was introduced to allow network devices to send messages back to the source of a message. This is an important feature to have, as the Internet Protocol (IP) does not natively return feedback itself.
IPv4 and IPv6
There are two versions of ICMP; ICMP for IPv4 and ICMP for IPv6.This article focuses on ICMP for IPv4
ICMP provides feedback about hosts and networks to the sender of an IP packet. The routers and switches along the network path are not notified about the errors. An example of ICMP error reporting includes ‘host/network not found’ when the destination endpoint can’t be reached.
ICMP does not include error correction, so this does not make IP more reliable. However, it does allow the sender to be able to handle the errors. The actual error handling is done with a higher layer protcols (such as TCP) or within the application itself.
To avoid creating error loops, ICMP does not send error notifications about other failed ICMP packets.
Another use for ICMP is to provide a better path for packets to take to a destination. For example, if a router receives a packet destined for network ‘A’, this router may know of a router with a better path. In this case the first router will send an ICMP redirect back to the sender, suggesting that it use the other router instead.
Troubleshooting is a third usage for ICMP. Examples of this include ping and traceroute, which send ICMP echo requests to determine whether a host is reachable, and the path taken to get there.
As ICMP is part of the IP stack at layer-3, it does not use ports to identify ‘flows’ or ‘streams’ of traffic. ICMP instead uses ‘control messages’, which are made up of a type and code value. In addition, some ICMP types use Identifier and Sequence numbers to track which process generated an ICMP request. In the case of errors, which are sent unsolicited by another host or router, part of the original IP packet is embedded into the ICMP payload, to match up the error with the process that sent the original packet.
Architecture
ICMP is separate from, but tightly integrated to IP. It is encapsulated in IP (protocol number 1), right after the IP header, but unlike other protcols in this situation, this is still considered to be layer-3 traffic.
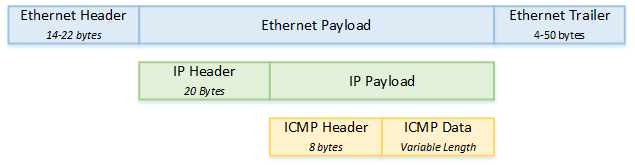
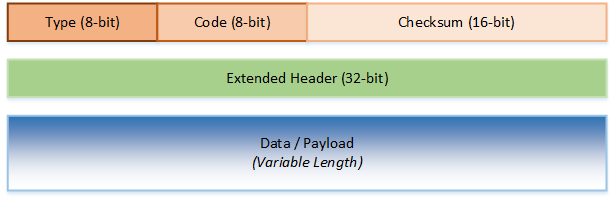
ICMP uses a header and data area. The header is 8 bytes long, and the data area can vary in length. The first four bytes of the header include the Type, the Code and a checksum.
The type defines what kind of ICMP message this is, such as Echo, Unreachable, and so on. The Code is only used by some types, and is used to give more information about an error.
The second half of the header (unofficially called the Extended Header on this site) is used to give additional feedback in some cases. It is not used by every message type, and can be left as zero in these cases.
Extended Header
ICMP is often used to report errors. Most errors will include the first 8 bytes of data from the original IP packet that caused the error in the ICMP payload (data error). This is used to help the sender match the error to the process that sent the original packet.
Common Usage
Some of the more common ICMP message types are listed in the table blow. For the full list, see the article on ICMP Types.
| Type | Description | Common Usage |
|---|---|---|
| 0 | Echo Reply | Ping and Traceroute |
| 3 | Destination Unreachable | Seen in ping when the end host can’t be reached |
| 5 | Redirect | Redirects a flow to a better router |
| 8 | Echo | Ping and Traceroute |
| 11 | Time Exceeded | TTL expiry messages |
| 12 | Parameter Problem | A ‘catch-all’ error |
| 13 | Timestamp | Clock Synchronization |
| 14 | Timestamp Reply | Clock Synchronization |
Ping and Traceroute
 Ping and traceroute are common ICMP-based tools, which use echo and echo-reply messages to determine if a host is on and responding, and the path traffic takes to get there.
Ping and traceroute are common ICMP-based tools, which use echo and echo-reply messages to determine if a host is on and responding, and the path traffic takes to get there.
To determine if a host is up, a sender will create an ICMP echo packet, and put a bunch of ASCII characters in the data area (payload). Depending on implementation, a timestamp may also be embedded.
If the destination successfully receives and processes the echo packet, it will respond with an echo-reply. The payload of the reply has to be identical to the payload of the echo.
If the ping in unsuccessful, the sender may get an ICMP error message from an interim device, such as an Unreachable if there is a routing or fragmentation problem, or Time Exceeded if the original packet got stuck in a loop.
Traceroute may also use ICMP echo, echo-reply, and time-exceeded messages to map out the path that a packet will take. This is used for diagnostic purposes, not to change packet flow.
Some traceroute implementations (such as in Windows) use ICMP. However, other implementations use UDP instead, or offer both options. The UDP implementation is not discussed here.
When a traceroute is started, the sender first creates an ICMP echo packet, and sets the TTL in the IP header to 1. When the first router receives this packet, it decrements the TTL to zero, and sends back a Time-Exceeded message. The sender then records the first hop in the path.
The sender then creates another echo packet, with a TTL of two. The first router decrements the TTL, and forwards the message to the second router in the path. The second router decrements the TTL to zero, and sends back the Time-Exceeded message. The sender then records the second hop in the path.
This process continues, with TTL’s incrementing each time, to get the entire list of routers in a path. This will continue until the destination is reached, or the traceroute fails for some reason.
Usually three packets are send for each hop, which helps diagnose availability of the hop, but also helps to reveal if there are multiple paths to a destination.
It is important to note that some devices ‘hide’ from traceroute, by not decrementing the TTL. The ASA firewall is one example of such as device.
Traceroute
Modern traceroute uses ICMP or UDP as described above. This should not be confused with ICMP type 30, which is a deprecated version of traceroute
Redirects
 A redirect is used to inform a host that there is a better gateway available for the destination it is trying to reach.
A redirect is used to inform a host that there is a better gateway available for the destination it is trying to reach.
An example of this is when there are two routers on the local LAN; Router-A and Router-B. Router-A is used for internet access and is the default gateway for hosts on the network. Router-B is used for WAN connectivity, and has specific routes in its routing table.
If a host on the network wants to send a packet to a destination over the WAN, it will send the packet to the default gateway (Router-A), relying on it to route the packet. When Router-A receives the packet, it looks at its routing table, and determines that Router-B is the best next-hop for this destination. Router-A then forwards the packet to Router-B.
Wanting to be a little more helpful, Router-A realises that the sending host and Router-B are on the same LAN. Router-A then sends a redirect message to the host, informing it that Router-B would be a better gateway for this network. The host will then use Router-B for future communications with this destination.
Routing Loop Notification
 Sometimes, sub-optimal routing leads to a loop in the network. As an example, this can happen if Router-A points to Router-B, Router-B points to Router-C, and Router-C points back to Router-A.
Sometimes, sub-optimal routing leads to a loop in the network. As an example, this can happen if Router-A points to Router-B, Router-B points to Router-C, and Router-C points back to Router-A.
With no loop prevention, a packet could be forwarded around these three routers indefinitely (at least until a router reboots, a link fails, routes change, and so on).
This problem is solved by the TTL field in the IP header. Each router decrements the value in this field until it reaches zero, and then the packet is discarded. This limits the number of hops that packet can pass over, based on what the source host sets the TTL to initially.
If there is a layer-3 loop in the network, the TTL will eventually drop to zero, and the packet will be discarded. The router that decrements the TTL to zero will then create an ICMP Time-Expired message, which is sent back to the original host.
Security

ICMP can be a very useful tool, however it can be abused, which may lead to security holes on the network. Below are a few ICMP-related security concerns, which can help admins to decide when to block and when to allow ICMP.
Footprinting
The first step in an attack is to gather information about the target. This is called ‘footprinting the network’, and ICMP can be very useful for this. Examples of footprinting via ICMP include ‘ping sweeps’ to find live hosts, and router discovery using Solicitation messages.
Many administrators will block ICMP entirely to prevent this type of footprinting. This does have some downsides, as it makes troubleshooting and monitoring a bit harder. A middle-ground is to block ICMP from untrusted networks (such as the internet) and allow ICMP internally.
Denial of Service
There are a few ways ICMP could be used to create a DoS or DDoS attack. Firstly, think about Unreachable messages. They tell a source host that a particular destination host is down or unavailable. If one of these messages were to be spoofed, this could trick a host into voluntarily closing a connection. An example of this is the Click tool, which disconnects IRC clients from their servers.
Another example is a Smurf Attack, where large numbers of Echo packets (pings) are sent from multiple source hosts (DDoS) to a target. This can overwhelm the target, causing it to spend more time working on handling the ping packets than processing legitimate traffic. Using a firewall’s ICMP rate-limiting feature may help mitigate this attack.
An older example is the Ping of Death. The largest IP packet allowed is 65535 bytes long. An operating systems may have a buffer for receiving these packets, and may set the buffer to be 65535 bytes long as well, as not packet can be larger. However, and attacker can create large custom fragmented packets, which the target tries to reassemble. The reassembled size is larger than the buffer, which causes an overflow, and may crash the Operating System. Modern operating systems have patched this flaw.
Tunnelling
Tunneling is a method of encapsulating one type of traffic within another type of traffic. From an attack perspective, successful tunneling means that restricted data or commands can be sent in and out of a system, while looking like ordinary traffic.
This can be done with ICMP echo and echo-reply packets. The data field of these packets is usually just ASCII text, which makes it suitable to hide other data in. What could look like a series of ping and responses could really be covert channeling, and it may be allowed, because many firewalls only look at the layer3 and 4 headers.
A mitigation for this would be using an application firewall or IPS that does deep packet inspection, and looks at the payload as well as the headers.
Man in the Middle
A Man-In-The-Middle (MITM) attack is where a compromised device intercepts legitimate traffic, and either forwards it on unaltered (but keep the information it learns from the traffic), or alters the traffic before forwarding it.
ICMP redirects can be spoofed, which cause a host to use a compromised router as its gateway for a particular destination network. An attacker can then use or alter the packets it receives as they wish.
References
IANA – ICMP Type Numbers
Network Sorcery – ICMP Internet Control Message Protocol
Wikipedia – Internet Control Message Protocol
Incapsula – Ping of Death
SANS – IDFAQ: I am seeing odd ICMP traffic, what could this mean?
Infosec Institute – ICMP Attacks
HITB Sec News – Footprinting: The Basics of Hacking
Informit – Anatomy Of A Hack—The Rise And Fall Of Your Network
The Legal Hacker – Use Ping Command in Footprinting
Great post, thank you.
You’re welcome!
Zaista interesantan tekst, mislim blog. Great post, thank you.
You’re welcome!