Does Your Network Need Some Firepower?
Sunday December 4, 2016
It Started at the End
AKA, It’s Good to Have All the Information Up Front
This story begins a few weeks ago at the end of a network design. Usually it is odd for a story to start at the end, but in reality, thats where things got interesting.
The team and I were designing a data centre network, used to support a hyper-converged compute platform. In the compute stack is a custom written suite of applications.
In the core, we used Nexus 9000’s. For firewalling the edge and DMZ, we used ASA 5500’s. And underneath the network lives a truck load of compute.
Nice and simple right? Of course not. It wouldn’t be interesting if it was simple, and the developers made sure it wasn’t.
At the 11th hour, we got a call from one of the developers, with concerns about throughput. He said there is an SQL server farm in the DMZ, which would generate at least 1Gbps of traffic to the inside network. The poor old 5525-x just can’t handle that kind of throughput, especially with Firepower.
So it’s time to rethink the design. We considered two basic ways forward from here. Use larger firewalls that can handle the throughput, or more firewalls to share the load. While looking into the larger firewalls option, I decided to have a look at the Firepower 4100 series.
The Firepower 4100 appliances are new on the scene, so I had to put in a bit of research. I aim to share with you the results of my research, to provide a high-level overview to these firewalls. As it turns out, they’re a bit different from the traditional ASA’s.

Enter the Firepower Appliances
When Cisco design firewalls, they tend to target three different families:
- SMB & Distributed Enterprise
- Commercial and Enterprise
- Data Centre, High Performance Computing, Service Provider
Firepower 9300 claims a 600% performance increase on the ASA 5585
Cisco targets the Firepower appliances at the high-performance / data centre market. Mid-2015 saw the release of the Firepower 9300 as a high throughput firewall/IPS. In fact, it has a 600% performance increase on the 5585. Unfortunately, this is out of the price range for many of us.
Luckily, in early 2016, Cisco released the Firepower 4100 series. This provides us with another option if we need more than the 5585 can provide. If you can’t justify the ludicrously expensive 9300, you can use the obscenely expensive 4100 series.
Been working with ASA’s for a while? Good news everyone! The Firepower appliances can run the traditional ‘ASA with Firepower Services’ image.
Do you like the idea of converging firewall and IPS functions? You’re in luck. The Firepower appliances can also run the Firepower Threat Defence (FTD) image.
If you havent heard about FTD yet, it is the new unified code image for ASA’s and Firepower appliances. It enables the appliance to run as both a firewall and Firepower IPS at the same time. This is a little different to ASA with Firepower, as they run as two separate software modules.
You can use Firepower Management Centre (FMC) to manage FTD for IPS and firewall rules. In contrast, ASA with Firepower Services can only have IPS services managed from FMC.
It appears that FTD will be the future of Cisco firewalls.

Software
There are two main types of software on the Firepower appliance. Platform Bundles and Applications.
FXOS, or Firepower eXtensible Operating System, is the Firepower operating system. For this reason, the Firepower appliance is also known as the FXOS chassis. FXOS consists of several images for managing the supervisor and security engine. Together, these are called the platform bundle.
The FXOS Chassis can run FTD or ASA images
The FXOS security engine can run different application images. These include FTD, ASA, or Radware’s DDoS services. At a high level, this is like running a virtual machine on a hypervisor.
Application images can be stored offline on the supervisor. These files are CSP (Cisco Secure Package) files. This may include various versions of the same image.
An administrator can then deploy the CSP’s to the security engine. The process of deploying an image known as logical device creation. These offline images are also used to update a logical device.
Remember to check that the FXOS version and the image version are compatible. Additionally, be aware that only one FTD or ASA image is deployed to the security engine at one time.
FXOS
FXOS does need a bit of special configuration. This does seem to be a ‘set and forget’ config on the 4100 series though.
To complete the initial configuration, use the CLI over the console port. On first boot, there is a text based wizard to run through. The wizard sets the management IP, host name, and configures an NTP server. NTP is mandatory, by the way.
The initial wizard does have a slight twist though. It allows you to restore an FXOS backup, rather than performing initial configuration. This becomes useful when a failed device gets replaced.
After the intial setup wizard is complete, it’s time for more configuration. You can continue using the CLI, or connect to the web interface.
The physical interfaces in the FXOS chassis are ‘owned’ by FXOS, not the security image (such as FTD). If you need etherchannels, configure them in FXOS first. They are then allocated to the security image. To me, this feels a bit like the system context on the traditional ASA.
There is no clustering across several FXOS chassis. The 9300 does support intra-chassis clustering, as it can run several security engines. In this case, an ASA image can run on two or more engines, and act as a cluster. The 4100 is different, as it only has one security engine. This means that there is no clustering at the FXOS level.
FTD Image
FTD is the new unified code set. It combines traditional firewalling and the Firepower IPS into a single image. The image is stored on the supervisor until its deployment to the security engine, where it runs on top of FXOS.
There are some differences in FTD, as compared to the traditional ASA software. There is not yet feature parity between the ASA image and the FTD image. Some noticable missing features are cluster and multi-context support. It is likely that these features will be an addition in the 6.3 release in around April 2017.
Another difference is that packets are natively inspected by Firepower. the ASA differs, as traffic is copied to the Firepower module for analysis. The FTD method is far more efficient.
The third major difference that I’d like to raise is management. Firepower Management Centre handles FTD management. The CLI is not used for configuration at all. The CLI is still useful for troubleshooting, and showing interface statistics.
The FXOS Chassis requires FMC for management
Unlike the ASA 5500, the Firepower appliance cannot be managed with the FDM. It requires FMC for management. If you’re not familiar with Firepower Device Manager, think of it as the ASDM replacement for FTD.
FMC is deployed as a physical or virtual appliance. The smallest investment you can make into FMC is a two device virtual appliance. Each ASA or firepower appliance consumes an FMC device license.
ASA Image
The traditional ASA image is still a viable option on the Firepower appliance. One reason for doing this includes the full list of features, which aren’t yet available on FTD. Another is having current skills available to support the firewall deployment.
I’m going to speculate, but I think that FTD will be the path forward for ASA and Firepower appliances. So, it’s important to consider whether it’s best to stick with the ASA image, or start fresh with FTD. Currently, moving from ASA to FTD requires reimaging, which erases the config. There is talk of a migration tool coming in the future (maybe in version 6.2).
Hardware
The 4100 is quite conservative in size, being only 1 unit high. This makes it the smallest of Cisco’s data centre firewalls. This is quite impressive when considering how powerful it is.
It has a power switch on the back; Just make sure you gracefully shut it down before flipping it off.
Interfaces

One of the best features of the Firepower 4100 is the 10Gb SFP+ interfaces. There are eight of them built in, as well as a 1Gbps SFP management port. This is a nice departure from the 1Gbps RJ45 ports on the smaller ASA 5500’s.
There are also two single-width expansion ports for extra interfaces. 1, 10, and 40 Gbps options are available. The only one missing here is the 100Gbps interface expansion. These are double-width, which are only supported on the Firepower 9300.
There are two options for interfaces; Hardware Bypass or Non-Hardware Bypass. Hardware bypassing supports fail-to-wire. If there is a failure in the interface, traffic can continue to flow through the appliance.
You might wonder why you would ever want traffic to pass through a firewall without inspection. The answer is that you probably wouldn’t. If the appliance is only acting as an IPS sensor, it may be preferrable for traffic to continue to flow. Definitely not something you would want for your edge firewall though.
Hardware Acceleration
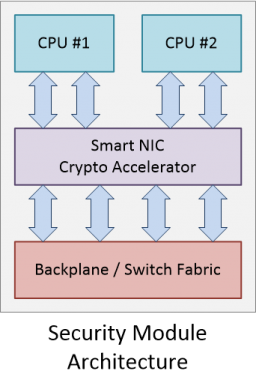
The 4100 appliances have a Smart NIC and a Crypto Accelerator. This is some advanced sillicon that enables offloading flows to hardware, for low latency. The Crypto Accelerator enables cryptographic offload for fast encrypt/decrypt operations and VPN acceleration.
The sillicon sits between each CPU and the internal switching fabric, bridging the two. For this reason, the 4110 (single CPU) has ony one Smart NIC / Crypto Accelerator. The rest of the models (dual-CPU) have two.
Model Comparison
All 4100 models use DDR4 memory, and support one or two SSD hard disks (at least one SSD disk is mandatory).
| Feature | 4110 | 4120 | 4120 | 4150 |
|---|---|---|---|---|
| Processor | 1x 12 Cores | 2x 12 Cores | 2x 18 Cores | 2x 22 Cores |
| Storage | 200GB | 200GB | 400GB | 400GB |
| Memory | 64GB | 128GB | 256GB | 256GB |
| PSU’s | Single, Dual optional | Single, Dual optional | Dual | Dual |
Each appliance has two SSD drive bays. The disk in bay number #1 is used for Firepower (and is mandatory). The second hard disk bay is only for MSP, or Malware Storage Pack.
The MSP disk is 800GB in size, and stores forensic and file data about malware for later analysis.
Throughput
In the end, the main concern is usually throughput. The table below compares the various 4100 models.
The table below uses the terms ‘firewall’, ‘AVC’ and ‘NGIPS’. ‘Firewall’ is regular ACL type traffic based on IP address and port numbers.
AVC (Application Visibility and Control) is deep packet inspection. In this case the firewall looks into the packet to determine the application in use.
NGIPS (Next-Generation IPS) is the Firepower inspection module througput.
All vendors use ‘magic’ numbers when representing their throughput. For network appliances, throughput is generally tested using 64 byte UDP packets. This is the best case scenario, and usually won’t reflect a real network. Think of the values below like a comparison rate at a bank. Useful to compare models, but it’s not what you will see in the real world.
| 4110 | 4120 | 4140 | 4150 | |
|---|---|---|---|---|
| Firewall | 35 Gbps | 60 Gbps | 70 Gbps | 75 Gbps |
| Firewall + AVC | 12 Gbps | 20 Gbps | 25 Gbps | 30 Gbps |
| Firewall + AVC + NGIPS | 10 Gbps | 15 Gbps | 20 Gbps | 24 Gbps |
| Max Sessions (AVC) | 9 mil | 15 mil | 25 mil | 30 mil |
| New Conn. per sec (AVC) | 68k | 120k | 160k | 200k |
Impressive stats… So how does this compare to the ASA 5585’s? I have tried to put the the 4110 appliance side-by-side with the higher-level 5585’s.
While reading the table, keep in the back of your mind that this is a rough comparison. There are several factors that will affect this. For example, whether the ASA or FTD image used.
For fair comparison, remember that the 5585 does not support FTD. This is because it implements a separate Firepower hardware module).
I recommend checking out the Firepower and ASA data sheets for more detailed information.
Additionally, remember that Firepower license costs take throughput into account. This means that the more throughtput an appliance has, whether it’s used or not, the higher the cost.
| 4110 | 5585 SSP40 | 5585 SSP-60 | |
|---|---|---|---|
| FW + AVC | 12 Gbps | 10 Gbps | 15 Gbps |
| FW + AVC + NGIPS | 10 Gbps | 6 Gbps | 10 Gbps |
| Max Sessions (AVC) | 9 mil | 1.8mil | 4mil |
| New Conn. per sec (AVC) | 68k | 120k | 160k |
As you can see, the Firepower 4110 appliance fits between the SSP-40 and SSP-60 on the 5585.
Conclusion
The Firepower 4100 appliance looks to be a solid option. It’s high-speed interfaces, hardware offloading, and tremendous throughput make it quite attractive. Yet, there are some small drawbacks:
- They can be quite pricey for smaller deployments
- There are still some features missing in software today
My personal opinion is that the Firepower appliances will begin to replace the 5585’s. I also think that FTD will replace the traditional ASA image in the long run. Only time will tell if this is the case.
So, what’s your opinion? Are the Firepower appliances worth the price tag? Do you prefer a different vendor?
Please leave a comment below.
