OSI Model
Last Updated: [last-modified] (UTC)
Introduction
 Hosts on a network need to communicate with each other. This is not as simple as it sounds. It requires different parts of hardware and software work together. They need to speak the same ‘language’.
Hosts on a network need to communicate with each other. This is not as simple as it sounds. It requires different parts of hardware and software work together. They need to speak the same ‘language’.
The different languages that network hosts speak are called protocols. Protocols are a defined set of communication rules, that are built into network software and hardware.
An example of network hardware is the Network Interface Card or NIC. An example of network software is the NIC driver.
Key point: The OSI model views the network as layers
A single host will use many different protocols to achieve different tasks. Usually, several protocols and systems are used together. An example of this is when you send an email. The email client and server communicate with a protocol called SMTP. But SMTP only describes how mail works. They also use protocols like TCP to make sure that the message arrives, IP addresses to know where to send the message, and Ethernet to convert the message to electrical signals.
It can be tricky to understand how all these parts fit together. To help with that, we can use the OSI model. This is a theoretical model that breaks the network components into layers. You may have heard of terms like ‘layer-3 switch’. The ‘layer 3’ part is referring to the layer in the OSI model.
Each layer represents part of the network on a host. The stack starts at the bottom with the physical layer and goes right up to the application layer. Each of the seven layers communicates with the layer above and the layer below.
The advantage of this is that an application, up in layer 7, does not need to know anything about how the physical network. The application just does its job and passes information to the layer below. The same is true in reverse. A NIC will receive bits of information, but it doesn’t care at all about the application that uses the data. It just focuses on receiving the bits and passing them up the stack.
As we look deeper, you will see that we don’t use the OSI model to describe specific protocols. It’s a method of showing how information in the network is handled, independant of the specific protocols in use.
How the Model Works
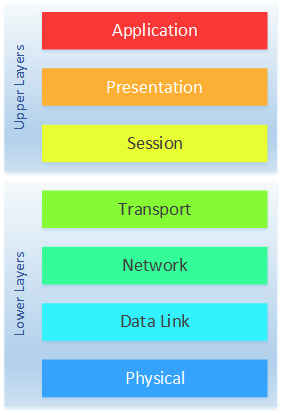 The OSI model consists of seven layers. Here is a quick overview from the top down.
The OSI model consists of seven layers. Here is a quick overview from the top down.
(7) Application – The parts of the network stack that communicates with the application. This includes network APIs
(6) Presentation – This layer translates the data between the application and the network
(5) Session – Builds and maintains a session between application processes
(4) Transport – Takes a stream of data, and breaks it into segments. This allows multiplexing on the network (allowing more than one traffic flow at once)
(3) Network – Provides addressing and routing services
(2) Data Link – Handles delivery of data between two nodes connected to a physical medium
(1) Physical – Transmits and receives data across a physical medium. This may be electrical, light, or radio signals
That’s a lot to remember! If it helps, try to use a mnemonic to remember the layers. Here’s one that you can use:
It’s a bit silly, but that’s what makes it memorable.
You might notice in the diagram on the right, that the layers are grouped into Lower Layers and Upper Layers. The lower layers (layers 1-4) are where most of the network components live, and where network engineers traditionally spend most of their time. The Upper layers (layers 5-6) are mostly application related, and where developers and application specialists traditionally spend more time.
Data Flow
When an application needs to access the network, it starts at layer 7. Data is passed down through the layers toward layer 1, with each layer performing necessary functions. When data is received by a host, it is received at layer-1 and works its way back up to layer 7, where the application is waiting.
When information is moving down the layers, some layers will encapsulate the data. Encapsulation is the process of adding more and more information. An example of this is at layer 3, where a destination IP address is usually added. Adding extra information like this aids in the delivery and handling of the original data.
Picture a piece of data as a block of ones and zeroes. During encapsulation, more data may be added to the front and/or the back of this block. Data added to the front is called a header, while data added to the end is called a trailer.
When information is received by a host, the process is reversed. Headers and trailers are removed as the data moves back up the layers until eventually the original information is left for the application to use.
You can see this process in the diagram below:
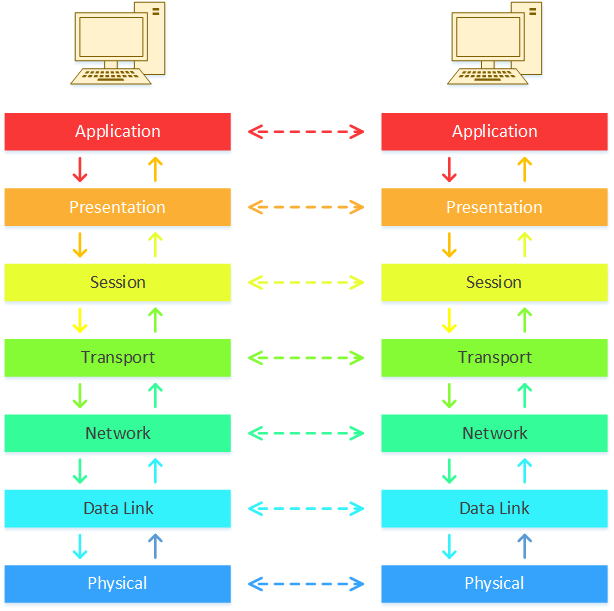
There are a few interesting things we can see here. First, we see that each layer communicates with the layer above and the layer below. They don’t communicate with any other layer.
Second, a layer on one host will logically communicate with the same layer on the second host. The application layer, for example, communicates with the application layer on the remote host. It doesn’t know any of the details that the other layers handle. This can be a little difficult to understand right now, but it will make sense over time.
Breaking it Down
Key point: Data is broken into chunks, and passes through the layers
When an application needs to access the network, it’s not overly concerned with how the data is formatted. All it is worried about is whether the application on the receiving host can understand it.
But this would not work well for a network. A network needs data to be broken into manageable chunks. There are a few reasons for this. Imagine that you’re transferring a large amount of data, and there’s a problem. If some of the data doesn’t make it, you have to start again. However, if the data is broken into manageable chunks, only the chunk that went bad needs to be resent.
On top of this, remember that there are many applications which might want network access. If the network is tied up with one large transfer, everything else will have to wait. But, with manageable chunks of data, applications can take turns accessing the network. More important data can even be prioritised over less important data.
Generally, each chunk of data is called a Protocol Data Unit (PDU). Each layer tends to have its own name for the data it works with:
- Layer 1 has bits
- Layer 2 works with frames
- Layer 3 has packets
- Layer 4 will use Segments or Datagrams, depending on how the data is used
We’ll now start to get a deeper understanding of what each layer does.
Layers
Layer 7 – Application
An interface between the application and the network
This layer is used to provide end users with network support. For example, this covers web browsing, emailing, and APIs.
Some common services here include accessing remote files and printers, directory services, and management sessions like SSH and RDP.
Layer 6 – Presentation
Negotiates the format of the data
The Presentation layer, AKA the ‘syntax’ or ‘translation’ layer, is used to convert data between the application and the network. Some examples of when this would be used include encryption, compression, graphics handling, and character conversion.
In a nutshell, it formats the data into something that the rest of the layers can easily use. This makes it possible for the data to be handled correctly, even if the underlying protocols change.
The sending host formats the data so it can be understood on the network. The receiving host converts the data back to a format that the application can use.
Layer 5 – Session
Groups messages into sessions
The Session layer establishes a connection between processes on different hosts. As the name suggests, each of these connections is called a session. Perhaps you’ve heard of Remote Procedure Call (RPC)? It runs right here in the session layer.
Each host may have many applications and services accessing the network at one time, which is why it is so important to track the sessions. This entails tracking the requests and responses between remote processes.
Layer 4 – Transport
Delivers or transports traffic between two endpoints
Here’s where the fun begins! We’re outside of the upper layers, and into the real networking! The Transport layer is used to transport data across the network without errors.
Part of its job is to segment the traffic into smaller blocks. This is completely transparent to the upper layers. When all the blocks are received at the other end, the recipient transport layer reassembles the blocks into the original data. This makes the flow of traffic appear to be a stream of data.
The most common protocols used at layer 4 are TCP and UDP. They’re huge topics on their own, so we won’t discuss them in depth here. Both TCP and UDP use port numbers to identify which traffic flow each block of data belongs to. TCP and UDP both add source and destination port numbers, along with other information, to the data segment in the form of a header.
Using port numbers makes it easy to track each flow, which in turn makes it easy to handle different flows in different ways. For example, if one flow is overwhelming the recipient, it can ask the sender to ‘back off’ on this flow. Network devices can also prioritise one flow over another, or block a particular flow entirely.
Another task of this layer is multiplexing. Multiplexing means that we can have more than one flow on the network at once. That’s a major advantage of breaking up the data into manageable blocks. Each flow can take turns sending their blocks of data. This means, for example, that you can receive mail while you are browsing the web.
Layer 3 – Network
Provides logical endpoint addressing and routing services
The network layer is one of two possible places that we use addressing. Most commonly, this is where we use IP addresses. It’s not surprising then, that this is also the layer where routing occurs.
At layer-3, a piece of information is called a packet. Routing occurs when a packet needs to move from one network to another. The actual routing (or traffic forwarding) between networks is done by a router.
To achieve its purpose, one of the things that the network layer does is add another header. This header includes the source and destination IP addresses, along with other information about the packet. The headers added by layers 3 and 4 are not usually changed as the packet moves about the network. There are technologies like NAT that are an exception to this, but we won’t get into them here.
As we’ll see soon, layer-2 can only handle a block of data up to a maximum size. So, part of the network layer’s job is to make sure that the packet is not too big. If a packet is too big, it will be broken into smaller chunks, called fragments. They are reassembled when they reach the destination host. Each fragment has its own set of headers.
Layer-3 is not required to be reliable. This means that it does not need to implement any error checking like the transport layer does. This is because other layers already do error checking.
Layer 2 – Data Link
Used to transfer data between network nodes over a specific network type
Data needs to be transferred between nodes on the same network segment. This may be a case where two hosts are on the same segment, or a host is sending data to a router. This is what the Data Link layer is all about.
But devices don’t just throw a handful of bits at each other. They’re a bit smarter than that. Instead, layer-2 establishes a logical link between the endpoints. This makes it possible to have hosts connected to a switch, rather than directly connected to each other.
 Just like layer-3, the data link layer uses addressing. One of the layer-2 address types that you will come across regularly is the MAC address. This comes from the address that is stamped onto your network card. When layer-3 passes a packet to layer-2, another header is added, which includes these addresses. This is no longer called a packet; It is now called a frame.
Just like layer-3, the data link layer uses addressing. One of the layer-2 address types that you will come across regularly is the MAC address. This comes from the address that is stamped onto your network card. When layer-3 passes a packet to layer-2, another header is added, which includes these addresses. This is no longer called a packet; It is now called a frame.
The network is usually made up of smaller networks that are joined together. For example, you may have a main office with a network, a branch office with a network, and a WAN network connecting them together. These networks may also use different connection types, such as Ethernet, WiFi, and PPP. That is one of the reasons that we need the data link layer.
It will build a channel of communication across one part of the network, for example from a host to the router. Then a separate layer-2 connection will be used to get from the head office router to the branch office router, which uses different cabling types. Another connection is then used to get from the router to the destination host. This is quite different to layers 3 and 4, which only thinks about the ultimate source and destination hosts.
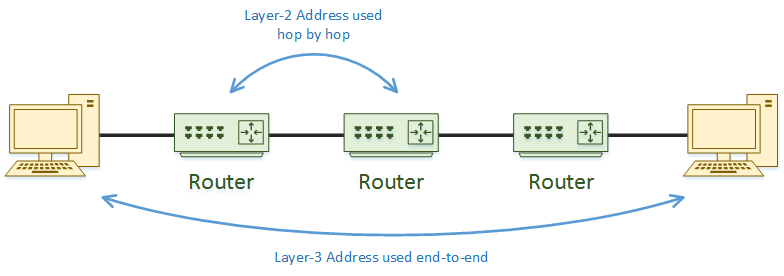
The data link layer is broken into two sub-layers. The Logical Link Control (LLC) layer is used to receive data from layer 3 and hand it to the Medium Access Control (MAC) sublayer. LLC’s primary job is to translate the layer 3 protocol (most commonly IP, but that’s not always the case) into something that the MAC sublayer can work with.
The MAC layer adds the headers and trailers to the packet to create the frame. It will also add information that can be used for error correction an handling.
Layer 1 – Physical
Defines the physical specifications of the network
The primary job of the physical layer is obvious. It needs to ‘get the data on the wire’ (or fibre or WiFi as the case may be). It deals with the raw stream of ones and zeros.
So, what this means is that the physical layer is interested in physical details. These include radio frequencies, pins, voltages, and how the bits are placed on the physical medium. This means that it needs to work out how to encode the information. For example, which electrical or radio states represent a one or a zero? Is the signal digital or analogue? How do we know when a frame starts and ends?
There are a few other devices beyond network cards, cables, and radio frequencies that fit in here too. These are ‘dumb’ devices which should not change the data. These include hubs, repeaters, and media converters.
TLDR – The Important Bits
These days the OSI model is just a model. It’s used for training and understanding how parts of the network fit together. It’s made up of seven layers, covering every network function from physical to the application.
When data is sent from or arrives at a host, it works its way through these layers. Each layer has their own job to do, which may include addressing, error handling, and reformatting the data.
A big stream of data is broken into manageable blocks of data, which can each be handled individually. In a process called encapsulation, these blocks have extra information added to them, in the form of headers and trailers.
Each layer communicates directly with the layer above and the layer below, as well as logically communicating with the corresponding layer on the remote host.
References
Wikipedia – OSI Model
Lifewire – The Layers of the OSI Model Illustrated
Techopedia – Transport Layer
Techopedia – Presentation Layer
Techopedia – Application Layer
OSI-Model – Session Layer
Microsoft – Windows Network Architecture and the OSI Model
InetDaemon – The OSI Model – Real World Example
Juniper – Data Link Layer Overview
Wendell Odom – CCENT/CCNA ICND1 100-105 (ISBN 1587205807)
Awesome!!!
I passed the CCNA already but I still don’t know much about the upper layers.
This article has clarified some common queries that I have during the time I work as a Networking engineer.
Thank you so much.