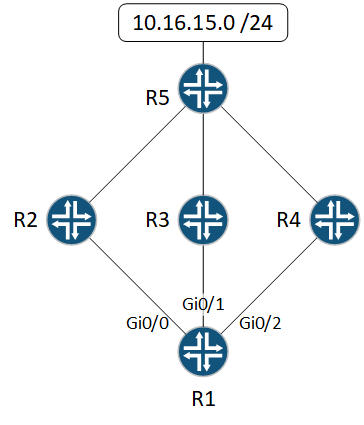
Lab Topology
In this lab we’ll get familiar with dynamic routing in general, without looking too deeply into any specific protocol.
In the topology below, dynamic routing is already configured. You will need to connect to R1 and investigate further.
Lab Files
| Initial Config | Dynamic Routing Lab |
| Completed | N/A |
See general lab information to get started.
Challenge – Scenario
Log onto router R1 and answer the following questions:
- What is the bandwidth of each link?
- Which routing protocols are in use?
- Which path to 10.16.15.0 /24 is preferred?
- What happens if we shut down gi0/0?
- How could we change this behaviour on this router only? Could this cause a problem?
Challenge – Solution
Question #1
To find the bandwidth of a link, use the show interface … command like this:
R1#show interface gi 0/0
GigabitEthernet0/0 is up, line protocol is up
Hardware is iGbE, address is 5254.0016.5fde (bia 5254.0016.5fde)
Internet address is 172.16.10.2/30
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Auto Duplex, Auto Speed, link type is auto, media type is RJ45
output flow-control is unsupported, input flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:02, output 00:00:01, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
198 packets input, 21635 bytes, 0 no buffer
Received 5 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 0 multicast, 0 pause input
279 packets output, 26831 bytes, 0 underruns
0 output errors, 0 collisions, 1 interface resets
0 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
From that output, we can see that the bandwidth is 1000000 Kbps, or 1Gig.
There’s a lot of information there, so we can use a slightly different command to simplify it:
R1#show interface | include BW
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
That quickly and simply shows that all interfaces are 1Gbps.
Question #2
To find the routing protocols in use, enter the show ip protocols command. The output is usually quite long, so we can add the summary keyword:
R1#show ip protocols summary
Index Process Name
0 connected
1 static
2 application
3 eigrp 10
4 ospf 10
*** IP Routing is NSF aware ***
Here we see that we’re running EIGRP and OSPF.
You might notice that there is application listed among the routing information. This is part of Cisco’s OnePK system, which you can ignore for now.
Question #3
To find the path to 10.16.15.0 /24, we need to look at the routing table:
R1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
D 10.16.15.0 [90/131072] via 172.16.10.1, 00:30:16, GigabitEthernet0/0
172.16.0.0/16 is variably subnetted, 9 subnets, 2 masks
D 172.16.0.0/30 [90/3072] via 172.16.10.1, 00:30:17, GigabitEthernet0/0
D 172.16.1.0/30 [90/3328] via 172.16.10.1, 00:30:16, GigabitEthernet0/0
O 172.16.2.0/30 [110/2] via 172.16.12.1, 00:29:20, GigabitEthernet0/2
C 172.16.10.0/30 is directly connected, GigabitEthernet0/0
L 172.16.10.2/32 is directly connected, GigabitEthernet0/0
C 172.16.11.0/30 is directly connected, GigabitEthernet0/1
L 172.16.11.2/32 is directly connected, GigabitEthernet0/1
C 172.16.12.0/30 is directly connected, GigabitEthernet0/2
L 172.16.12.2/32 is directly connected, GigabitEthernet0/2
Here we can see that the next-hop to 10.16.15.0 is 172.16.10.1, using interface Gi0/0. This has been learned by EIGRP (the D code on the left of the route means EIGRP).
From our topology diagram we can see that the path is R1 — R2 — R5
Question #4
Now to shut down gi0/0…
R1(config)#int gi0/0
R1(config-if)#shut
R1(config-if)#^Z
How has this affected routing? Let’s look at the routing table:
R1#show ip route
! Excluding codes to save space
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
O 10.16.15.0 [110/3] via 172.16.12.1, 00:01:08, GigabitEthernet0/2
[110/3] via 172.16.11.1, 00:01:08, GigabitEthernet0/1
172.16.0.0/16 is variably subnetted, 6 subnets, 2 masks
O 172.16.1.0/30 [110/2] via 172.16.11.1, 00:01:08, GigabitEthernet0/1
O 172.16.2.0/30 [110/2] via 172.16.12.1, 00:35:13, GigabitEthernet0/2
C 172.16.11.0/30 is directly connected, GigabitEthernet0/1
L 172.16.11.2/32 is directly connected, GigabitEthernet0/1
C 172.16.12.0/30 is directly connected, GigabitEthernet0/2
L 172.16.12.2/32 is directly connected, GigabitEthernet0/2
We can see that shutting down gi0/0 causes the EIGRP neighbour relationship to drop. Fortunately there’s two other paths through to 10.16.15.0, which goes through R3 and R4.
We have some ECMP routes here. If you were to traceroute to 10.16.15.1, you would notice that both paths are used.
These were learned through OSPF. OSPF is (by default) less preferred than EIGRP. So these paths, although just as good, are only used if EIGRP is not working.
Question #5
In some ways, it’s better to use the OSPF paths in this topology. This is because there are two paths to use, not just one. That’s about 2Gbps of bandwidth, which is better than the 1Gbps of the single link.
Can we change this? Yes, first though, let’s put the EIGRP link back into play:
R1(config)#int gi0/0
R1(config-if)#no shut
R1(config-if)#^Z
Now the Gi0/0 path will be preferred again. We can change this by changing the default Administrative Distance. We could either lower the AD of OSPF, or raise the AD of EIGRP:
R1(config)#router ospf 10
R1(config-router)#distance 80
That lowers the AD of OSPF to 80, which is less than EIGRP (90). This is on this router only. The AD on other routers won’t change.
The effect is changing the routing table:
R1#show ip route
! Removing codes to save space
Gateway of last resort is not set
10.0.0.0/24 is subnetted, 1 subnets
O 10.16.15.0 [80/3] via 172.16.12.1, 00:01:31, GigabitEthernet0/2
[80/3] via 172.16.11.1, 00:01:31, GigabitEthernet0/1
172.16.0.0/16 is variably subnetted, 9 subnets, 2 masks
D 172.16.0.0/30 [90/3072] via 172.16.10.1, 00:02:59, GigabitEthernet0/0
O 172.16.1.0/30 [80/2] via 172.16.11.1, 00:01:31, GigabitEthernet0/1
O 172.16.2.0/30 [80/2] via 172.16.12.1, 00:01:31, GigabitEthernet0/2
C 172.16.10.0/30 is directly connected, GigabitEthernet0/0
L 172.16.10.2/32 is directly connected, GigabitEthernet0/0
C 172.16.11.0/30 is directly connected, GigabitEthernet0/1
L 172.16.11.2/32 is directly connected, GigabitEthernet0/1
C 172.16.12.0/30 is directly connected, GigabitEthernet0/2
L 172.16.12.2/32 is directly connected, GigabitEthernet0/2
From this we can see two things:
- The OSPF routes are now active, not EIGRP
- The AD/metric of the OSPF routes are [80/3]
Could this cause a problem? Not necessarily, but things definitely do change. Consider this… R1 now prefers the OSPF route to reach anything on R5.
What about R5? It has to send traffic back to R1. What route does it prefer? It will still prefer the EIGRP route. Remember, that AD is set on each router, and there’s no guarantee that they will match.
So, if we ping 10.16.15.1 from R1, the traffic will go:
- R1 –> R3/R4 –> R5
- R5 –> R2 –> R1
The return path is different! This is called asymmetric routing. For routers like this, it’s not a problem. But when we start looking at firewalls, or if NAT is involved, we may have trouble…