
Firepower Management Centre
Last Updated: [last-modified] (UTC)
Back in the old days, Cisco had an IPS called the ASA CX Module. It wasn’t great. But, if there’s one thing that Cisco is very good at, it’s finding companies with good tech and buying them out.s with good tech and buying them out.
SourceFire was one of these companies. SourceFire had a very good IPS product. It made the CX module look like the slow kid eating paste at the back of the classroom. In late 2013, Cisco acquired SourceFire and replaced the old CX module with Firepower.
As part of the acquisition, Cisco took over a product called FireSight Defence Centre. Over time it was re-branded to Firepower Management Center. FMC manages firepower appliances and gives you with insight into your security.
In this article, we’ll have a high-level look at Firepower Management Centre.
Firepower Overview
 Firepower comes in several different flavours. One option is ASA with Firepower Services. This is the traditional ASA, with the Firepower IPS running as a software module. This is a similar deployment model to the old CX module, but with more features. They run as two different operating systems on a single device.run as two different operating systems on a single device.
Firepower comes in several different flavours. One option is ASA with Firepower Services. This is the traditional ASA, with the Firepower IPS running as a software module. This is a similar deployment model to the old CX module, but with more features. They run as two different operating systems on a single device.run as two different operating systems on a single device.
Another option is Firepower Threat Defence (FTD). This is a unified code image. It combines the traditional ASA firewall and the Firepower IPS. This is much newer and lacks some of the mature features that ASA with Firepower services has. This is where Cisco is aiming their development, so expect new features on a regular basis. This image may run on the ASA 5500-X series appliances, or on one of the newer Firepower appliances.
The Firepower 7000 or 8000 series appliances can use Firepower. But, these only have IPS features and lack the traditional ASA firewalling components.
Finally, there is a virtual appliance called FTDv. This is the Threat Defence code, that runs on a hypervisor.
FMC is capable of managing all these options in some form. It is unable to manage the traditional ASA firewall. This limits its features with ASA with Firepower Services.
FMC Deployment
You may deploy FMC as a physical or virtual appliance. When selecting the type of appliance you need, consider:
- The number of sensors you want to manage
- The number of ‘events’ you need to keep
- The amount of storage in the appliance
- The number of network hosts that can be detected
A virtual appliance is an easy place to start. The largest is capable of managing 25 sensors, storing 50m events, and detecting 50,000 hosts.
Remember to choose well. If you buy the small 2-sensor virtual appliance, you can’t upgrade that to a 10-sensor appliance. You need to install the extra virtual appliance and migrate over to it. Or, you can leave your sensors on different FMC’s, which is not ideal.

Firepower Features and Licenses
Firepower contains four main licensed features:
- T – Threat
- A – Applications
- M – Malware
- C – Content Filtering
Licenses will have some sort of combination of these features. For example, you may buy a TAMC license, which licenses all features. Or, you may buy a TA license, which only licenses Threat and Application Protection. Not every combination is available.
Licensing is configured in FMC, and applies to both FMC and the appliances that it manages. Depending on the appliance, the licensing needs to be classic or smart licenses.
Besides these main licenses, VPN licenses are also available.
The FMC Getting Started Guide shows how Smart and Classic licenses are configured
[maxbutton id=”4″ text=”FMC Getting Started” url=”https://networkdirection.net/FMC+Getting+Started”]
Threat (Control)
The Threat license is also known as the Control license. The appliance comes with this license when you buy it, and it does not expire.
This license includes basic user and application control. This allows us to create Access Control Policies (covered later). This also allows configuration of HA pairs.
For this license to be effective, a Protection license is also required. Also, a TA subscription allows you to get system updates.
Applications (Protection)
The Application license, AKA the Protection license, comes with the appliance. Like the control license, it does not expire.
This license enables the IPS, file control, and security intelligence functionality. For these to be truly effective, add a TA subscription. This gets updates from ThreatGrid/Talos, which provides insight into new security threats.
The IPS feature uses the SNORT engine to perform deep packet inspection. This looks beyond the packet headers, to match patterns in the payload with known attacks.
File Control allows Firepower to look at files that are being transferred over HTTP, email, and so on. This can block or whitelist files. The Malware license can augment this.
Security Intelligence is a list of known bad IP’s and domains, based on risk. This list can be dynamically updated with the TA subscription.
Configuration guides on File, Intrusion, and Access Control policies
[maxbutton id=”4″ text=”File Policies” url=”https://networkdirection.net/File+Policies”][maxbutton id=”4″ text=”Intrusion Policies” url=”https://networkdirection.net/Firepower+Intrusion+Detection”][maxbutton id=”4″ text=”Access Control” url=”https://networkdirection.net/FMC+Access+Control+Policies”]
Malware (AMP for Firepower)
 The Malware license enables AMP for Firepower. This is a subscription based license. It protects against malware on the network edge. It can be integrated with AMP for Endpoints.
The Malware license enables AMP for Firepower. This is a subscription based license. It protects against malware on the network edge. It can be integrated with AMP for Endpoints.
When Firepower sees a file, it creates a hash of the file to check for known malware. The hash may also be sent to the AMP Cloudfor unknown files.
If a file enters the network, it is tracked. This is the file’s trajectory. If it is later found to be malware, we are able to use this information to see how it has propagated through the network.
Content Filtering
The Content Filtering subscription enables reputation based URL filtering. This feature allows blocking URL’s based on category or threat score. The URL lists are regularly updated by Talos. The subscription allows us to download the updates.
Without this license, URL filtering is still possible. The limitation is that this would not from a regularly updated list.
Safe Search is part of most search engines. It is able to filter certain content from the search results. If required, Firepower can enforce the use of Safe Search. This also extends to YouTube EDU. This is a limited version of YouTube, which only provides educational content. This is especially useful in schools or environments with children.

FMC Policies
FMC has a strong focus on policies. There are many different kinds of policies, which push settings to devices. This is much easier than configuring individual devices, like you would with ASDM.
Some policies target specific devices. Other policies need a parent policy before their settings take effect.
When changing a policy, it needs to be deployed to the appliances. This means that the appliances keep a copy of the settings locally. This allows them to continue working if they lose contact with FMC.
Below is a summary of the common policies in FMC.
Health Policies
 Health Policies specify the criteria that marks a device as healthy or unhealthy. For example, the policy may say that the device is unhealthy if the CPU is over 80%.
Health Policies specify the criteria that marks a device as healthy or unhealthy. For example, the policy may say that the device is unhealthy if the CPU is over 80%.
Alerts can then be configured based on the results of the policy. These policies apply to devices and FMC appliances.
Platform Settings Policies
 Platform settings are device specific settings. These include NTP servers, login banners, SMTP servers, and so on.
Platform settings are device specific settings. These include NTP servers, login banners, SMTP servers, and so on.
These policies apply to devices only.
Access Control Policies
![]() Access Control Policies, are like advanced ACL’s. They allow or deny traffic based on the given criteria. These policies apply to devices.
Access Control Policies, are like advanced ACL’s. They allow or deny traffic based on the given criteria. These policies apply to devices.
ACP’s are very important, as they bind a lot of other policies together. For example, if you have an Intrusion Policy, it won’t apply to the device directly. Instead, it links to the Access Control Policy.
This is also where advanced checks take place. These include Security Intelligence and Malware filtering.
Intrusion Policies
 Intrusion Policies are the IPS component of Firepower. This is where you can define IPS rules, and enable or disable them. These policies link to an Access Control Policy.
Intrusion Policies are the IPS component of Firepower. This is where you can define IPS rules, and enable or disable them. These policies link to an Access Control Policy.
Firepower also allows custom IPS recommendations. It bases these recommendations around what it has learned about your network.
NAT policies
![]() NAT rules go in NAT policies. This makes NAT rules reusable across different devices, creating consistency.
NAT rules go in NAT policies. This makes NAT rules reusable across different devices, creating consistency.
Configuring a NAT policy is like configuring NAT in the ASDM. There are options for Manual NAT, and Auto-NAT.
NAT policies apply directly to devices.
DNS Policies
 This allows the blacklisting or whitelisting of entire DNS domains. Any traffic that matches an entry in a DNS policy is not subject to any more checks.
This allows the blacklisting or whitelisting of entire DNS domains. Any traffic that matches an entry in a DNS policy is not subject to any more checks.
DNS policies link to an ACP.
Identity Policies
 Identity policies combine with Realms to authorise and provide insight into user activity. A realm represents LDAP or Active Directory domains.
Identity policies combine with Realms to authorise and provide insight into user activity. A realm represents LDAP or Active Directory domains.
These policies link to ACP’s.
File Policies
 File policies can allow or block files, or scan them for malware. This only applies to traffic types that are capable of carrying files (such as FTP, HTTP, and SMTP).
File policies can allow or block files, or scan them for malware. This only applies to traffic types that are capable of carrying files (such as FTP, HTTP, and SMTP).
A file policy optionally attaches to a rule in ACP. If the ACP rule matches, and traffic is not blocked, then the file policy is evaluated. Depending on the outcome, the policy may log, block, or allow the file.
Network Discovery
 Network discovery detects hosts on the network. Firepower uses this information in different ways.
Network discovery detects hosts on the network. Firepower uses this information in different ways.
One way to use this information is track files as they propagate through the network. Another is to build a vulnerability list. Firepower uses this list to recommend IPS rules to enable and disable.
SSL Policies
 If the appliance encounters encrypted traffic, it won’t be able to analyse it. SSL policies tell Firepower how to handle this type of situation. For example, Firepower can use a certificate to decrypt and scan the traffic. Also, it can be a man-in-the-middle, and decrypt then re-encrypt traffic as is passes through. This links to an Access Control Policy.
If the appliance encounters encrypted traffic, it won’t be able to analyse it. SSL policies tell Firepower how to handle this type of situation. For example, Firepower can use a certificate to decrypt and scan the traffic. Also, it can be a man-in-the-middle, and decrypt then re-encrypt traffic as is passes through. This links to an Access Control Policy.
Prefilter Policies
![]() Prefiltering is a way to implement simple ACL’s. Traffic passes through a pre-filter policy (if one exists) before it reaches an ACP.
Prefiltering is a way to implement simple ACL’s. Traffic passes through a pre-filter policy (if one exists) before it reaches an ACP.
One reason to do this is to allow or block certain traffic without submitting it to a deep packet scan. For example, if your network should not send emails out, a prefilter policy can block SMTP traffic.
Prefilter policies may allow traffic, which bypasses all other checks. An example of this is ICMP traffic, which you may not want to waste time scanning. Once a prefilter policy allows traffic, it is on the FastPath.
Even though prefilter policies are evaluated before ACP rules, it is still tied to an ACP policy.
Correlation Policies
 Correlation policies respond to realtime events on the network.
Correlation policies respond to realtime events on the network.
When certain conditions exist, the policy can take defined actions. An example of this is when Firepower finds a new host on the network. A correlation policy can use this event to cause FMC to run an NMAP scan on the new host.
Configuration guides on File, Intrusion, and Access Control policies
[maxbutton id=”4″ text=”File Policies” url=”https://networkdirection.net/File+Policies”][maxbutton id=”4″ text=”Intrusion Policies” url=”https://networkdirection.net/Firepower+Intrusion+Detection”][maxbutton id=”4″ text=”Access Control” url=”https://networkdirection.net/FMC+Access+Control+Policies”][maxbutton id=”4″ text=”NAT Policies” url=”https://networkdirection.net/FMC+NAT+Policies”][maxbutton id=”4″ text=”Network Discovery” url=”https://networkdirection.net/Network+Discovery”][maxbutton id=”4″ text=”Prefiltering” url=”https://networkdirection.net/Prefilter+Policies”][maxbutton id=”4″ text=”Identity” url=”https://networkdirection.net/Identity+and+Authentication”]

Dashboards and Analysis
FMC includes a Dashboard and an Analysis section. The dashboard and Context Explorer give us quick ‘at-a-glance’ information about the network. The Analysis section provides more detailed information and queries.
In the dashboard, you are able to ‘drill into’ areas to analyse it further.
Dashboards
Dashboards are in the Overview tab of FMC. There are several pre-defined dashboards ready to go, which will cover most of your needs. You can add your own dashboards if you want.
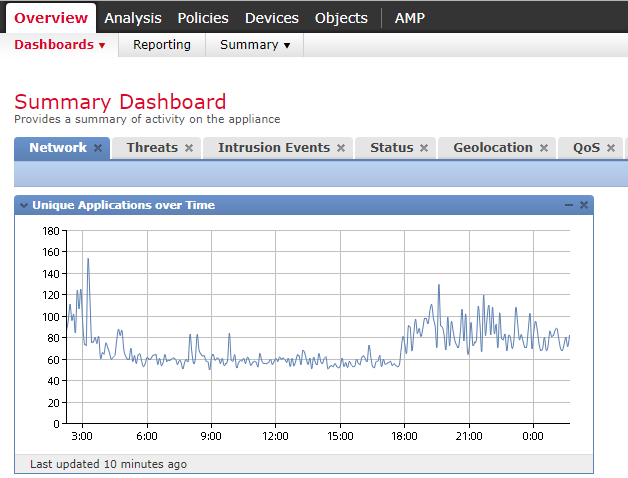
Each dashboard contains one or more widgets. In the screenshot, the Network dashboard contains the Unique Applications over Time widget. Further tune this by customising widgets to meet your needs.
Context Explorer
The Analysis tab has a lot of good information available. For now, we’ll focus on the Context Explorer.
The Context Explorer provides a graphical overview of the health of the network. In the example below, you can see Indications of Compromise in the network. This lists the attacks that Firepower has seen on the right, and the hosts it applies to on the left. IP addresses are not shown in this image.
While not shown below, Context Explorer can also give you insight into other parts of the network. This includes applications, connections, geolocation information, intrusions, hosts, files, and URL’s.
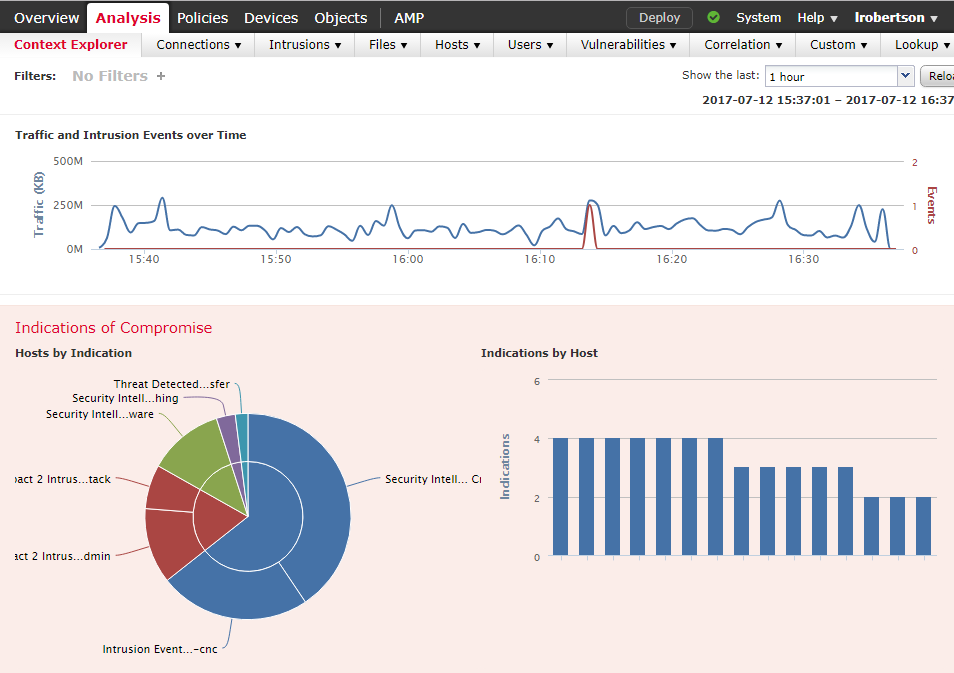
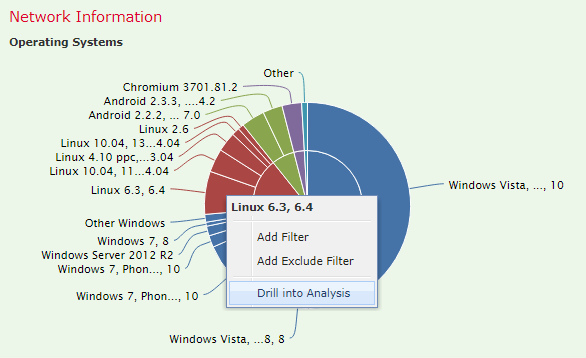
You can query most parts of the Context Explorer for more information. Left-click on any chart or graph to see a list of options.
Some useful options include:
- Drill into Analysis, which provides an extra level of detail
- Whois, which runs a WhoIs lookup on an IP
- View Host Information, which shows detailed information on a discovered host
- View User Information, which shows detailed information on a discovered user
References
Cisco – Firepower Management Center Configuration Guide, Version 6.2: Dashboards
Cisco – Security, Internet Access, and Communication Ports
Cisco – Security Intelligence Blacklisting
Todd Lammle – Cisco FirePOWER / Sourcefire Overview
Cisco – Licensing the Firepower System
Cisco – Using the Context Explorer
Hi,
This text is duplicated on the first paragraph “s with good tech and buying them out”
All the buttons are missing in this page. Excellent content, by the way.