
Network Discovery
Last Updated: [last-modified] (UTC)
Firepower can learn about the users, applications, and hosts on the network. Firepower uses this for monitoring, access control, customising IPS rules, and other functions.
The IPS rule customisation is of particular interest. FMC builds a list of your hosts, their operating systems, and the applications they run. With this, it can recommend ways to tune the intrusion policies. For example, if you don’t have any old NT servers, you don’t need to look for attacks that only target them.
There are two ways to detect hosts on the network; Actively and Passively.
Passive detection is the default method. Firepower analyses traffic that passes through to glean host information. It can also look at NetFlow data to get more information.
If the host is behind NAT, it may be difficult to determine its Operating System and applications. In this case, FMC will make a best guess, and assign a confidence score. You can create custom Operating System or application ‘fingerprints’ for better accuracy.
The active method improves accuracy by pulling information from more sources. Examples of active discovery include NMAP scans, or manually adding host information.
Discovery
There is a single discovery policy. You cannot create more policies, ore remove this one.
A single rule default rule discovers applications passively. You need to add more rules to detect users and hosts.
The policy is only evaluated if traffic is allowed through an Access Control Policy. Blocked traffic is not evaluated.
Rules
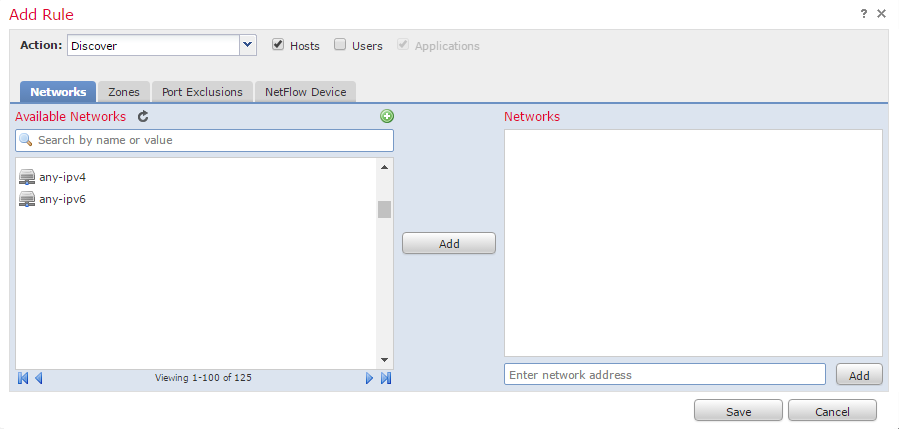
To add custom rules:
- Browse to Policies -> Network Discovery
- Click Add a Rule
- Set the action to Discover
- This could be set to Exclude to exclude networks from discovery
- Select Hosts and Users
- Applications will also be enabled by default
- Add the networks to perform discovery on
- On the Zones tab, add the zones that the rule should apply to
- Save the rule
The policy needs to be deployed to take effect. As there is only one policy, this will automatically apply to all managed devices.
Firepower will begin discovering traffic immediately. Over time, discovery information will appear in the Dashboard and Analysis areas.
Fingerprints
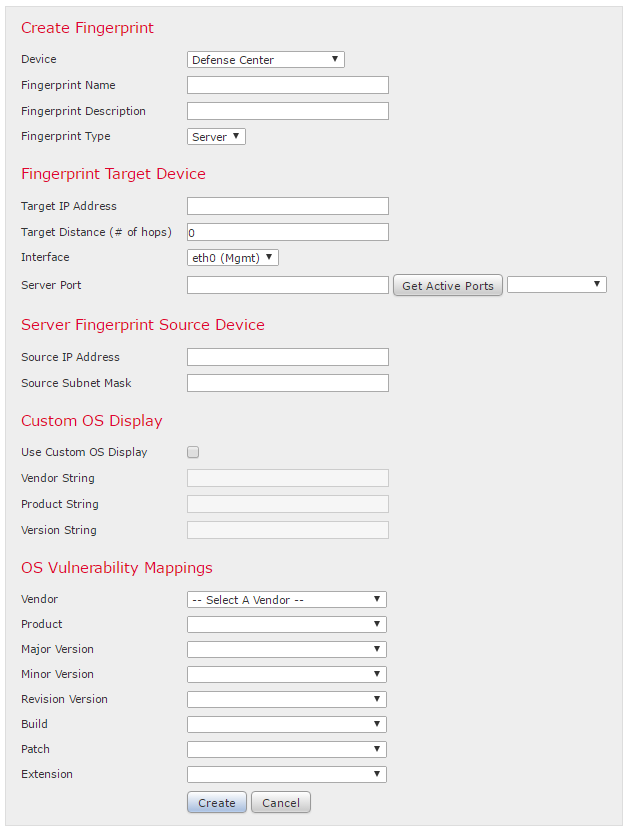
Custom fingerprints are used to more accurately detect Operating Systems. To create a custom fingerprint:
- Browse to Policies -> Network Discovery
- In the upper right corner, click Custom Operating Systems
- Click Create Custom Fingerprint
- Enter the details as required
References
Cisco – Introduction to Network Discovery and Identity