Question 1 & 2
Question 1:
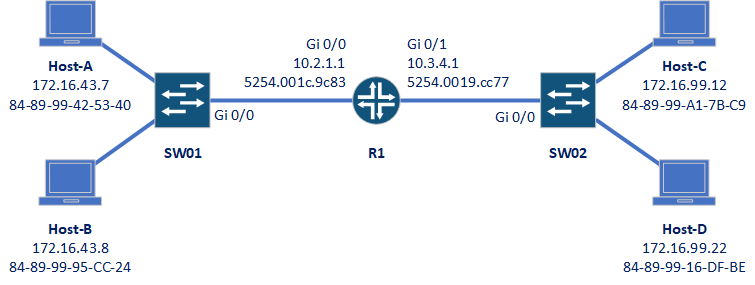
Host-A wants to send a packet to Host D. What will the source and destination IP and MAC addresses be?
Source IP: 172.16.43.7
Destination IP: 172.16.99.22
Source MAC: 88-89-99-42-53-40
Destination MAC: 5254.001c.9c83
Explanation:
The source IP and MAC are from Host-A itself.
The destination IP will be the IP of Host-D. IP addresses work at layer-3, which has both a network portion and a host portion. Therefore the end IP is what we need.
The destination MAC however, will be the MAC of the router. MAC addresses work at layer-2, which is interested in delivering frames hop-by-hop. The first hop will be the router, so the frame will be addressed to the router.
Notice that the MAC addresses are listed in different ways? MACs can be written in various forms, but they are all just MAC addresses.
Question 2:
Host-A wants to send traffic to Host-B. Which ports on the switch will the frame be sent out?
This depends on the traffic being sent out.
If a Broadcast were being sent, it would be forwarded out all switch ports. The router would not pass it on to SW02 though.
If A unicast packet were sent out, it would depend on the MAC address table on the switch.
If there were no entry for the destination MAC, the frame would be flooded out all ports. The switch would learn the correct entry for the MAC table from the reply.
If there is already an entry in the MAC table, the packet would be forwarded only out the port listed in the table entry.
Question 3
How many subnets can we have on a single VLAN? How many should we have?
we should have only one subnet per VLAN.
Why? Because the VLAN and subnet both provide a boundary, and they align well.
If we have more than one subnet per VLAN, what could happen? Occasionally, devices in different subnets would see broadcast and flooded messages from the other subnet. This would break security, which is one of the main reasons that we use VLANs in the first place.
Remember the rule: One subnet per VLAN
Question 4
How can we verify which VLANs exist on a switch?
There are two ways we might do this.
The first way is to run show running-config, and look for VLAN configuration.
The second simpler way is to use show vlan brief.
Question 5
Why might it be dangerous to take a switch that was previously in production, and put it in a new production network?
Because of VTP.
If the switch happens to be running as a VTP server, it may propagate its VLAN configuration through the production network, changing VLAN configuration.
It is recommended to turn on the switch while not connected to the production network, and change the VTP mode to transparent, or erase the switch configuration.
Question 6
Based on the MAC address table shown below, which port is likely configured as a trunk?
SW01#show mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 5254.0002.fcc8 DYNAMIC Gi0/1
1 5254.0007.7055 DYNAMIC Gi0/1
1 5254.0013.10e9 DYNAMIC Gi0/0
1 5254.0019.853c DYNAMIC Gi0/1
1 5254.001c.7a83 DYNAMIC Gi0/1
Total Mac Addresses for this criterion: 5
Port gi0/1
We can tell this because there are multiple MAC addresses being learned on the same port, indicating that a switch is attached.
Question 7
How can we find out which interfaces are configured as trunks?
There are two ways.
Option 1 is to use show running-config, and look at each interface. See which ones are configured with switchport mode trunk or DTP.
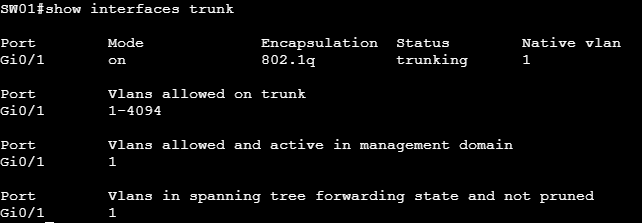
Option 2 is to use the command show interfaces trunk
Question 8
How can we see if a particular interface is operationally acting as an access port or a trunk port?
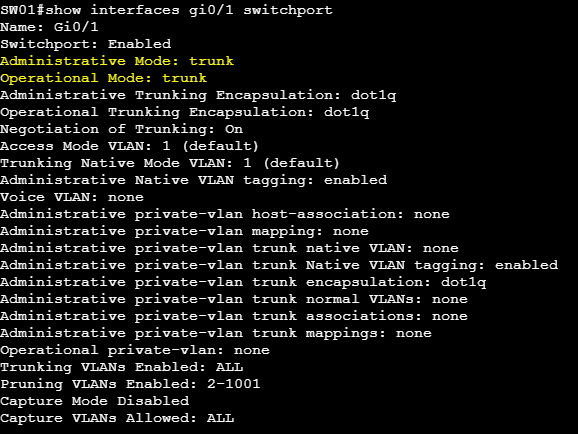
Of course, we can look at the running config, but a better way is with show interfaces <interface> switchport
Question 9
How can we add more VLANs to a trunk, without overwriting the existing VLAN list?
First, let’s imagine that we have VLANs 10 and 20 on a trunk link, and that we want to add VLAN 30.
switchport trunk allowed vlan 10,20
If we simply ran the command switchport trunk allowed vlan 30, this would overwrite the list, and prevent VLANs 10 and 20 from being allowed.
This means we have two options. The first is to overwrite using a complete list of all VLANs we want on the link:
switchport trunk allowed vlan 10,20,30
The alternative is to use the add keyword to add VLAN 30 to the list:
switchport trunk allowed vlan add 30