
File Policies
Last Updated: [last-modified] (UTC)
File Policies unlock AMP for Firepower. File and Intrusion policies combined form deep packet inspection.
File policies attach to certain rules in an Access Control Policy. Only traffic types that can carry files, such as FTP and HTTP, can benefit from file policies. When traffic matches one of these rules, firepower uses the file policy to determine the risk of the file. This may send file information to the AMP cloud or perform local analysis.
A file policy may also block files completely. This is file control, and is evaluated first. If the file isn’t blocked, then deeper malware inspection can take place.
Data from the AMP cloud can augment AMP for Firepower. If you have AMP for Endpoints in your network, you can feed this data into FMC. This shows detailed threat propagation and other information.
File inspections follow these steps:
- Spero Analysis – Firepower gets the signature of executable files and submits it to the AMP cloud
- Local Malware Analysis – Uses a local engine to check for malware. Unknown files or possible risks warrant further inspection
- Dynamic Analysis – Sends files to AMP ThreatGrid for further inspection
Policies
File policies are in Policies -> Access Control -> Malware and File
Click New File Policy to begin, and enter a name and description.
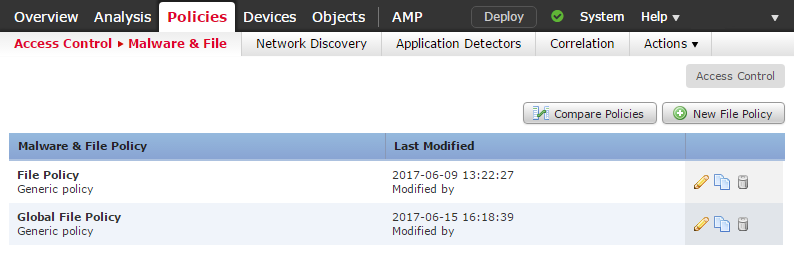
Rules
File policies are a colection of rules. Unlike ACP’s, these are not ordered rules.
Rule evaluation takes place in this order:
- Simple file blocking
- Malware inspection
- Simple detection and logging
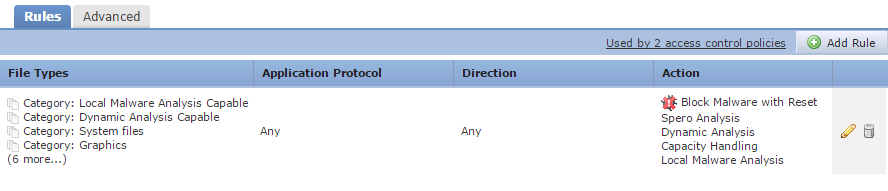
The advanced tab, general settings:
- First Time File Analysis – Sends a file to ThreatGrid if the appliance hasn’t seen it before. If this is not used, these files will be marked with an ‘unknown’ disposition
- Enable Custom Detection List – Enables a customised detection list
- Enable Clean List – Enable a whitelist of allowed files
- Mark Files as malware – Files are marked with a threat score. If files are above the threshold, they are marked as Malware. The higher the value, the higher the risk of false positives
Archives can also be inspected. The archive scanning options are also on the advanced tab:
- Inspect Archives – Enables or disables archive inspection. Changing this option causes a SNORT process restart
- Block Encrypted Archives – Block files if the contents are encrypted
- Block Uninspectable Archives – If an archive can’t be inspected for any reason other than encryption (for example, corruption), the file will be blocked
- Max Archive Depth – The maximum number of nested archives that can be scanned. The first nested file is a depth of one
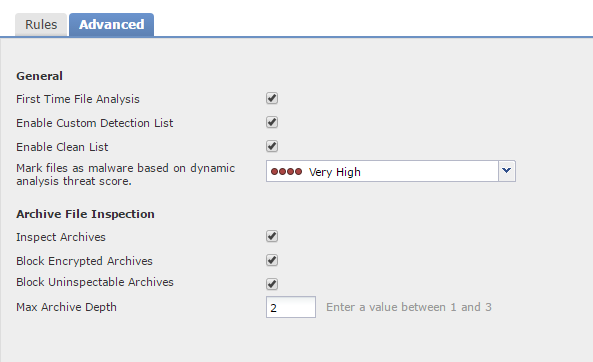
Rule Configuration
The Application Protocol specifies the protocol to scan. Only HTTP, SMTP, IMAP, POP3, FTP, and SMB are available. Some of these protocols can be scanned in an Upload direction, a Download direction, or both. Vaguer these conditions lead to mode scanned files, and lower performance.
The File Types and File Type Categories specify which files to scan. Once again, the more file types, the lower the performance.
There are several actions available:
- Block Files – Outright blocks certain file types
- Block Malware – Use local or AMP analysis to determine if the file is malware, and block it if it is
- Malware Cloud Lookup – Query AMP for file disposition information, but allow the file through
- Detect Files – Log the file, but allow the file through
Some actions allow additional options:
- Spero Analysis – Analyse MSEXE files, and send the signature to ThreatGrid
- Dynamic Analysis – Send the file to ThreatGrid for additional analysis
- Capacity Handling – If a file cannot be sent to ThreatGrid, store the file for now and analyse it later
- Local Malware Analysis – Use the local engine to determine if the file is malware
- Reset connection – Send a TCP reset. If disabled, the connection will be left to timeout
Blocked files (either outright or as part of a deep scan) can be stored on the appliance for later analysis.
One strategy is to use a file blocking policy to block any file types that you definitely do not want on the network. Then, create a policy that performs an analysis on anything that’s left.
References
Cisco – File Policies and AMP for Firepower