
FMC NAT Policies
Last Updated: [last-modified] (UTC)
When you’re running Threat Defence, configuration is not applied directly to the device. Instead, policies define configuration, which FMC deploy to the appliances.
NAT is no exception, which is a bit of a mind-shift if you’re used to using ASDM or the command line.
In FMC, a NAT policy consists of several NAT rules. If you’re familiar with configuring NAT in ASDM, you will feel quite at home as this part is quite similar.
What about ASA with Firepower services? NAT is still applied in the old fashion in this case, not through FMC. NAT policies are only for Threat Defence.
Rules
Policy Assignment
To find NAT policies, browse to Devices -> NAT. There’s nothing in here by default, so you will need to start by creating an empty policy.
A policy may be either Firepower NAT or Threat Defence NAT. The Threat Defence NAT policy applies to anything running the FTD image. This includes ASA X-Series and Firepower appliances. The Firepower NAT policy applies to IPS appliances, like the 7000 or 8000 series.
The rest of this article focuses on the Threat Defence NAT policy.
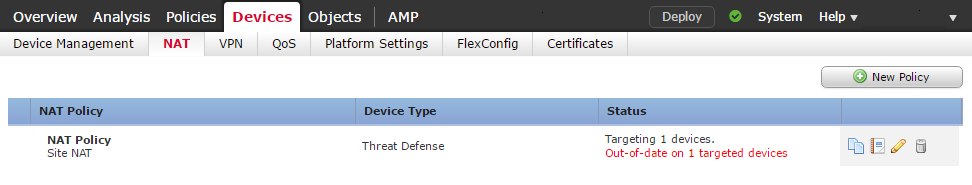
When creating a policy, it may be assigned to a device. In the screenshot above, the policy applies to a single ASA. A policy does not need to target a device. This allows us to pre-configure the policies before deploying it. If a device has a NAT policy applied, and an empty policy replaces it, FMC removes the existing NAT rules.
A single NAT policy may target many devices. This is useful, as it allows NAT policies to be consistent across many firewalls. This allows NAT to work if traffic reaches a different edge device during a failure or upgrade.
Each device may only have a single NAT policy applied.
Automatic and Manual NAT
 A NAT rule can be Auto-NAT or Manual NAT. This may feel familiar if you’re used to using ASDM.
A NAT rule can be Auto-NAT or Manual NAT. This may feel familiar if you’re used to using ASDM.
Auto-NAT rules are easier to configure and are the recommended approach in most cases. Unlike ASDM, you cannot apply Auto-NAT to an object. This is because different policies can reuse the objects.
Auto-NAT rules match traffic based on a source or destination object. Once it has found a match, it can apply the translation. This rule type will only translate the source address. If you need more advanced matching or translation, use Manual NAT
Manual NAT rules are more flexible, at the cost of being more complex. These rules can match traffic based on source and destination IP address and port number.ion address, as well as source and destination port.
Manual NAT rules are especially useful to creating NAT exemptions. These rules prevent any translations from taking place.
Static and Dynamic Rules
 A rule may be Static or Dynamic. A static NAT is quite simple. This binds one real IP to one translated IP. Static NATs have a bi-directional capability. This means that traffic originating at the destination will still have NAT applied.
A rule may be Static or Dynamic. A static NAT is quite simple. This binds one real IP to one translated IP. Static NATs have a bi-directional capability. This means that traffic originating at the destination will still have NAT applied.
A Dynamic NAT translates a group of real addresses to a pool of translated IP’s. This uses a one-to-one mapping.
A variation of this is Dynamic PAT. Dynamic PAT will translate one or more IP’s to a dynamic port. This is commonly used to provide internet access at the edge of the network. This is also known as Port Overloading.
Rule Order
Rules fit into one of three different categories. Firepower evaluates these categories in order, and applies the translation to the first match.
The three categories are:
- NAT Rules Before
- Auto NAT Rules
- NAT Rules After
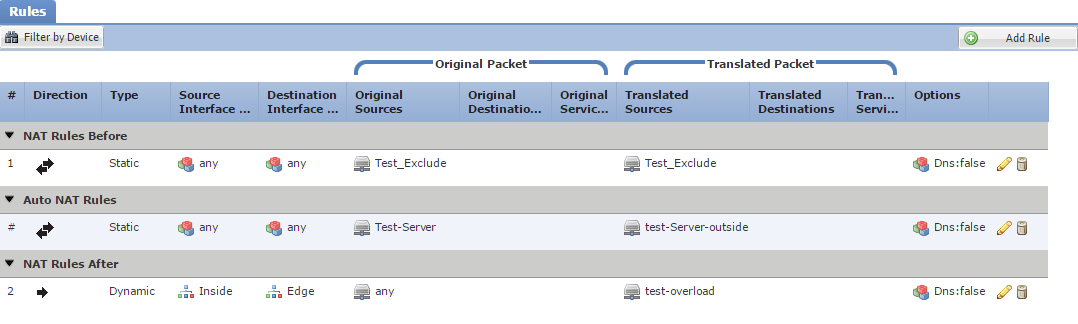
‘NAT Rules Before’ and ‘NAT Rules After’ are manual NAT rules. Each rule in these sections has a number, which determines the order of evaluation.
Auto NAT rules are different, as they do not have an order specifically applied. They follow the following rules:
- Static rules are evaluated before dynamic rules
- Rules with the smallest number of real IP addresses are evaluated before rules with more real IP’s
- If the number of real IP’s is the same, the lower IP values are evaluated first (for example, 10.10.10.10 is lower than 20.20.20.20)
- As a final tie breaker, the object name is evaluated in alphabetical order
Rule Configuration
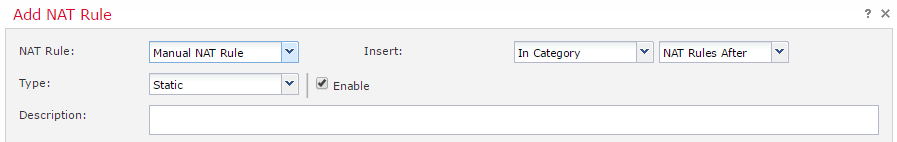
When creating a new rule, you can choose to make it a Manual or Auto-NAT rule. The screenshots below are set to Manual NAT Rule, as this enables the most options. This is also where the rule is set to Static or Dynamic.
The Insert section is available for manual rules. This determines the order of rule evaluation. If set to In Category, the rule can be in the Before or After section.
A manual rule also allows adding a description.
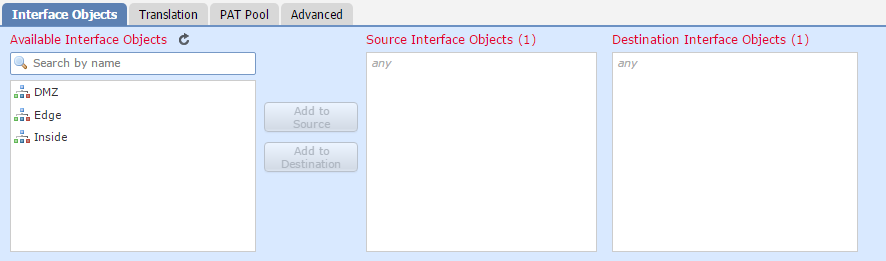
Interface Objects
Use this tab to select source and destination zones. This is used for matching traffic.
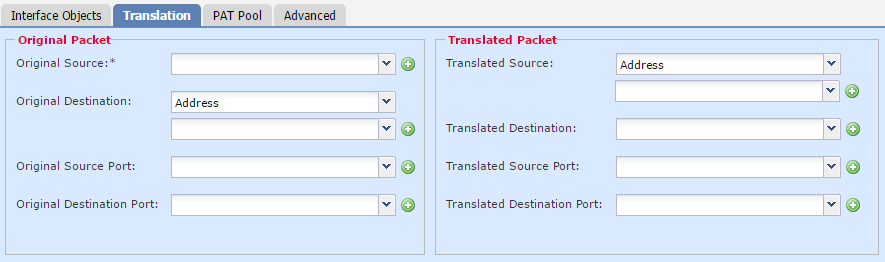
Translation
Translation has two sections. One is Original Packet, which is the conditions to match to. The other is Translated Packet, which is the action to take. The original packet is also known as the Real Address.
An Auto-NAT rule only uses the source address and port when matching and translating. Manual NAT can match and translate source and destination addresses and ports.
In both cases, the Translated Source may be the IP of the egress interface or an object.
PAT Pool
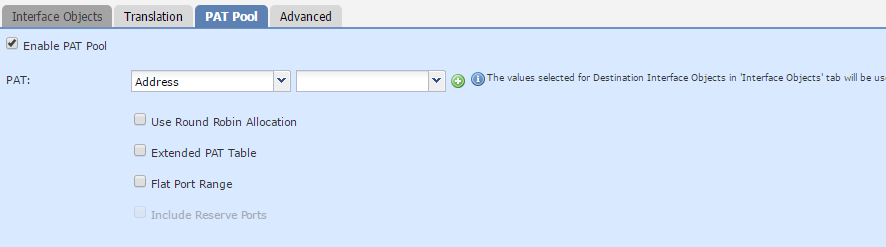
The PAT Pool option is available when using dynamic translations. More options become available when enabling this option.
The PAT type can be set to an Address or an interface IP. When using Address, you need to create an object that contains a pool of IP addresses.
Enabling Round Robin Allocation assigns the IP’s in the pool evenly. A source port from one IP is allocated, then the next request will take a port from the next IP address, and so on. If not enabled, all ports from one IP are used until they are exhausted. Then, we move onto the next IP in the pool.
By default, the translation table tracks the traffic flow’s source port. When using a pool of IP’s, the Extend PAT Table option may be useful. This enables Firepower to track the source and destination port in the table. This makes the PAT apply per service, rather than per IP. The purpose of this is to allow more port combinations per IP in the pool, extending the life of the pool. The drawback is that this is more resource intensive. Many application inspections do not work with this option.
With PAT, Threat Defence attempts to keep the same source port after translation. But, it’s not always going to work, as sometimes the port will have already been taken. Enabling Flat Port Range tells Threat Defence to use a port that’s close to the original source port. It does this by dividing all the source ports into groups of 512 ports. When the original source port is unavailable, it will then try to use a port in the same block. Use this option if you need to avoid using up all the low ports.
If the Flat Port Range is on, Include Reserve Ports becomes available. By default, translation only uses ports from 1024 and above. This option extends this to all ports.
Advanced Settings
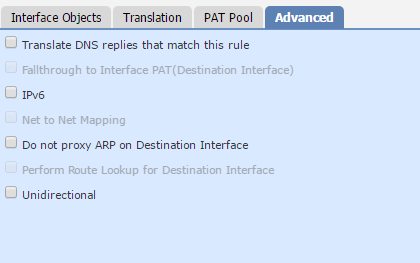
Translate DNS replies that match this rule rewrites the IP address in DNS responses.
Sometimes, the PAT pool gets exhausted. The Fallthrough to Interface PAT option allows using the IP of an outside interface in this case.
If you enable the IPv6 option, interface PAT uses the IPv6 address of the interface.
During migration to IPv6, the Net to Net Mapping for NAT46 option may be of use. This enables a one-to-one translation of IPv4 to IPv6 addresses.
By default, proxy ARP simplifies routing. Do not proxy ARP on Destination Interface disables this behaviour.
If identity NAT is used (in routed mode), the Perform Route Lookup for Destination Interface option is available. This uses the routing table to decide which interface to use for NAT.
Static NAT rules are bidirectional by default. This means that traffic initiated from the ‘destination’ address is still translated. This may be set to Unidirectional. This is where traffic is only initiated from the ‘source’ address.
References
Cisco – NAT Policy Management
Cisco – Network Address Translation (NAT) for Firepower Threat Defense