
Firepower Prefilter Policies
Last Updated: [last-modified] (UTC)
Pre-Filtering
Pre-Filtering is the optional first step of access control. A pre-filter policy contains rules that match simple values, like IP’s and ports. There is no deep packet inspection in a pre-filter policy.
One of the reasons to use this is to quickly allow or deny traffic, without deeper inspection. For example, imagine that you don’t allow SMTP traffic on your network. You could create a pre-filter policy that blocks TCP port 25. This doesn’t pass the traffic to the SNORT engine or check a malware policy. It blocks the traffic without wasting more resources.he traffic without wasting additional resources.
Traffic can also be put on the Fast-Path. The fast-path allows traffic while bypassing deeper inspection. For example, you may want to allow ICMP traffic for troubleshooting. You could add this to the pre-filter policy with an action of fast-path, saving resources.
If pre-filter policy rules do not match, the Access Control Policy takes over.
Pre-filtering is only supported on Threat Defence. ASA with Firepower Services cannot use pre-filter policies.
Passthrough Tunnels
 Tunnels carry traffic over a transport layer. An example of this is carrying IPv6 traffic over IPv4 during migration. Another example is separating tenants with GRE tunnels. These examples are different to tunnels across the internet, which encrypt their contents.
Tunnels carry traffic over a transport layer. An example of this is carrying IPv6 traffic over IPv4 during migration. Another example is separating tenants with GRE tunnels. These examples are different to tunnels across the internet, which encrypt their contents.
Tunnels cause a small issue for security devices like ASA’s. Tunnels have a set of outer headers and a set of inner headers. The outer headers describe the tunnel, and the inner headers describe the payload. If we were to filter based only on the outer headers, threats in the payload may get overlooked.
Firepower looks at the inner headers of an unencrypted tunnel. The pre-filter policy inspects the outer headers and blocks unauthorised tunnels. Authorised tunnels are then passed to the ACP for deeper inspection.
The pre-filter policy may rezone tunnel traffic. A tunnel may represent several traffic flows, not only one. A pre-filter policy can assign these connections to a logical zone. This allows the ACP to handle these connections in a more intelligent way.
Policy Configuration
Policies
Pre-Filter policies are in Policies -> Access Control -> Prefilter.
Firepower includes a single default policy. This policy passes all traffic through to ACP for deep inspection. Firepower uses this policy by default when you create a new ACP.
The default policy can only have limited changes made. You can change the default action and the logging settings, but you cannot add new rules. The best option is not to change the default policy at all.
Instead, create a custom policy by clicking New Policy. Make the required changes to the custom policy, then apply it to your ACP.
Rules
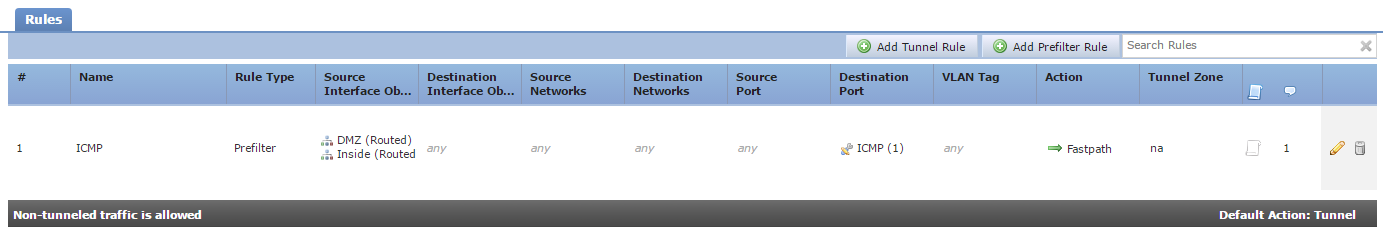
Policies are a series of rules, as shown below. There are two types of rule available:
- Prefilter – This is a normal ACL style rule, used to block or fastpath traffic. Traffic can also be passed to the ACP for deep inspection
- Tunnel – These rules block, fast-path, or rezone a plaintext tunnel
Each policy has a default action. The default action only applies to tunnel traffic. All other unmatched traffic is sent to the ACP for deep analysis.
Any tunnel traffic that doesn’t match one of the rules in the policy will have the default action applied. This may be blocking the tunnel traffic or passing it through to the ACP for deep analysis.
Prefilter Rule Configuration
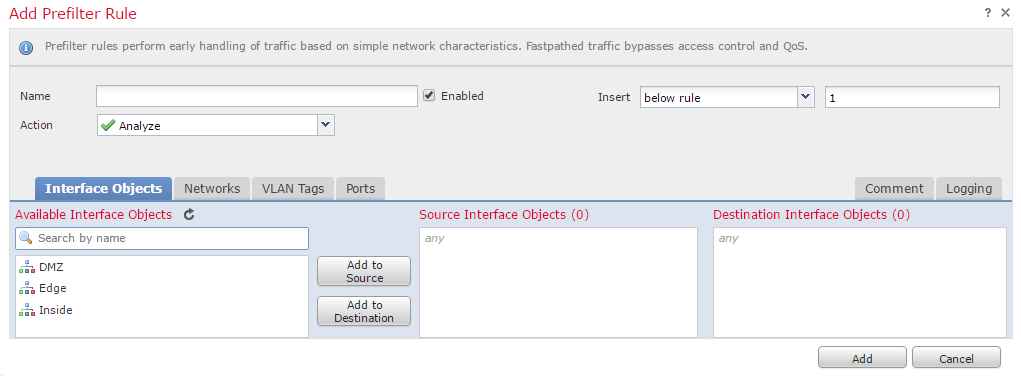
Click Add Prefilter Rule, and add in the basic information like the Name, and where the rule is inserted.
The Action can be set to:
- Analyze – This will pass traffic to the ACP for deep analysis
- Block – Drops traffic that matches the rule
- Fastpath – Adds traffic to the fast path. This traffic bypasses any extra inspections
There are a series of conditions that may be specified to match traffic. This includes source and destination interfaces, IP addresses, VLAN tags, and port information.
Logging generates events. Logging is required to see information in the dashboard and analysis sections.
References
Cisco – Prefiltering and Prefilter Policies